Securing your Microsoft 365 tools with ESET Cloud Office Security
Created: 2020-10-30 06:50:00
Attackers do go after businesses in the cloud
Without a doubt, one of the most common cloud services powering businesses today is Microsoft 365. Microsoft reported that the number of commercial monthly active users of Microsoft 365 tipped past the 200 million mark in the first quarter of the 2020 fiscal year.
As the number of businesses relying on Microsoft 365 grows, it is important to keep in mind that it is not just business employees who need protection, but also IT administrators who need the right tools to properly secure any assets hosted in Microsoft 365 from cyber attack.
This is especially notable considering that threat actors have a particular interest in targeting IT admins. Naturally, admins have privileged levels of access that, if compromised, allow an attacker to more easily deliver malware to other devices in a corporate network, steal data and set ransomware loose.
BleepingComputer, for example, reported how fake emails warning about expired Microsoft 365 licenses and unauthorized access to Microsoft 365 email accounts were being sent to IT admins. The goal of such scam emails was to trick admins into clicking on links that redirected to fake Microsoft 365 login pages asking for their admin credentials.
Microsoft 365 emails are in the billions, and so are phishing emails
In 2018, Microsoft scanned more than 470 billion Microsoft 365 emails every month for phishing and malware. Of the total inbound emails, the 2018 high for the percentage of phishing emails detected was 0.55% in November, which increased to a 2019 high of 0.85% in July:
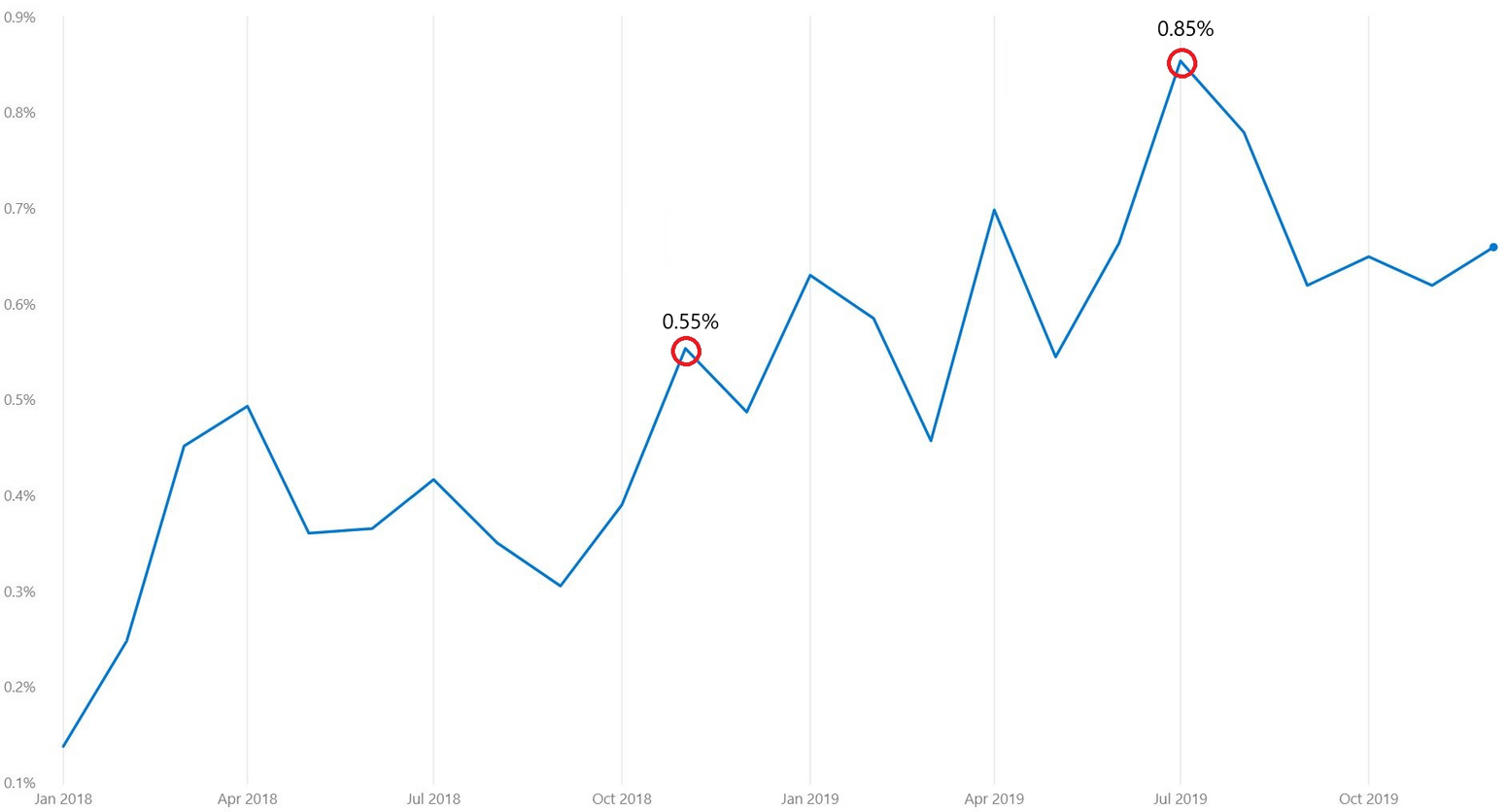
Figure 1: The percentage of inbound phishing emails in Microsoft 365 increased from a 2018 high of 0.55% to a 2019 high of 0.85%, according to Microsoft telemetry.
Just to give more meat to these numbers, 0.55% of 470 billion emails represents around 2.6 billion phishing emails. This is where ESET Cloud Office Security (ECOS) can help businesses protect employees from dangerous emails. ECOS adds a crucial layer of security on top of the built-in protection in Microsoft 365 by taking advantage of ESET’s award-winning engine, the same as used in ESET Mail Security, to scan all incoming and outgoing emails and attachments in Exchange Online for spam, phishing and malware:
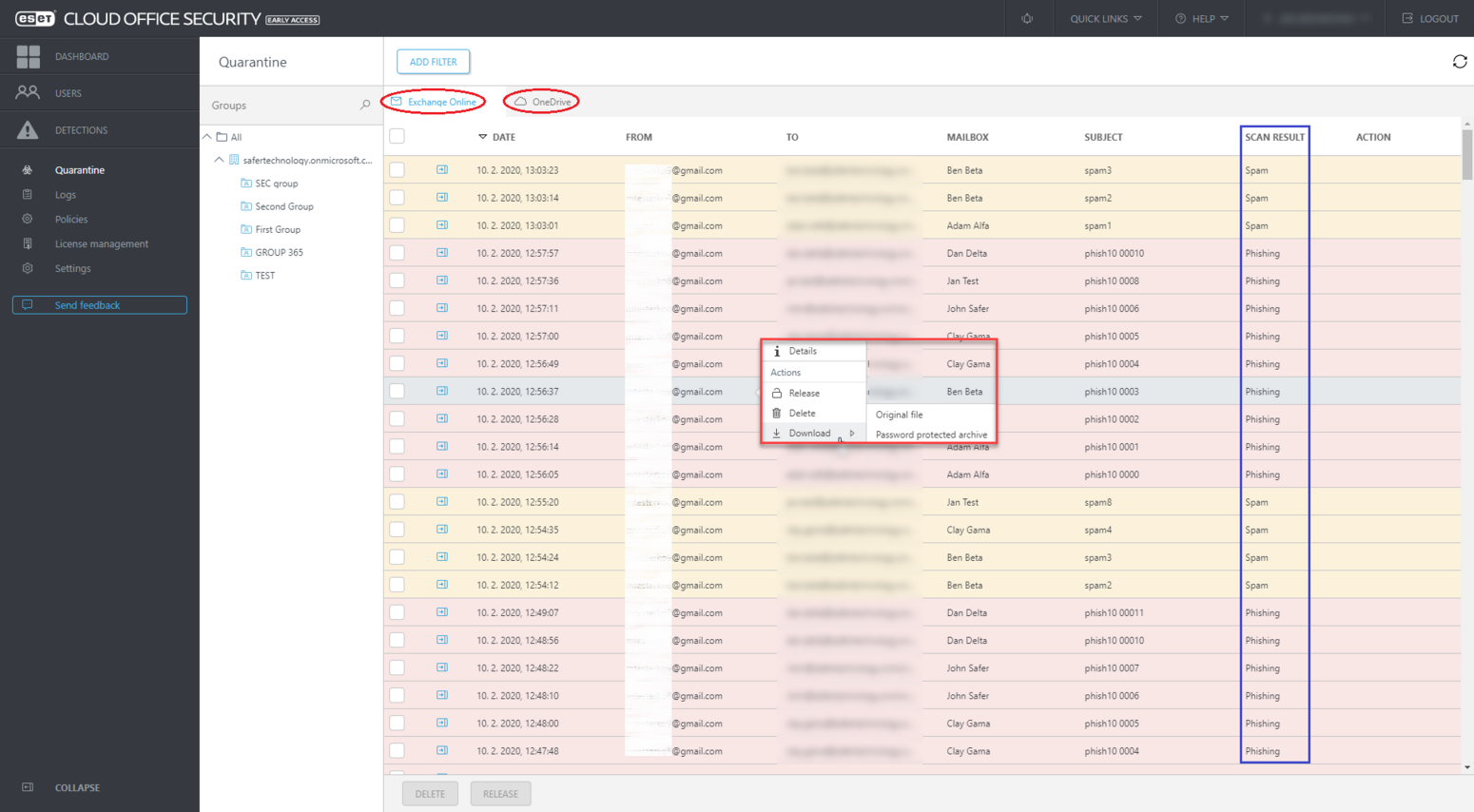
Figure 2: Quarantine view in ESET Cloud Office Security
ECOS quarantines suspicious emails and can automatically trigger an email notification to allow admins to take immediate remediation steps. This includes the possibility to look at further details about the quarantined emails and either delete or release them. Admins can also set up ECOS to automatically delete or move detected items to the junk or trash folders.
In addition, ESET Cloud Office Security integrates with OneDrive to scan all files for malware. This greatly helps businesses to lock down malware before it can spread in their environments and disrupt business continuity.
Admins can access the ECOS dashboard remotely through any major browser. The dashboard provides a range of views and capabilities useful for admins including:
1. Detection statistics
The ECOS dashboard provides an overview of users that have received the most spam, malicious and phishing emails, the top suspicious OneDrive accounts, and dedicated views for Exchange Online and OneDrive detections. If an admin needs to see at what times malware, spam and phishing detections are peaking, ECOS also provides hour-by-hour traffic numbers.
2. Detection filtering and identification
Checking your environment for indicators of compromise (IOCs) is a quick way of identifying the presence of attackers in your network. Common places to gather IOCs are in news reports and threat intelligence data feeds. With ECOS, admins can take the hashes of recently discovered malicious files and run a search in their Microsoft 365 environment for any matches. Detection filtering in ECOS can be done not only based on hashes, but also on tenant, action taken, subject, sender, recipient, name of user, scan result, detection name, owner name and owner object.
3. Accountability
If no detections are found after deploying ECOS, does this mean that ECOS is not protecting users? No. By checking the logs, admins can see that while ECOS is scanning emails and files, all items so far are free from malware, phishing and scams.
4. Custom protection settings
It is likely that certain groups of users in your Microsoft 365 environment will need the flexibility offered by tailor-fit protection settings. For example, a competitive intelligence team would be better served with looser antispam settings to ensure that all marketing communications from competitors are received.
For other teams, however, spam is likely to be a problem that can distract employees. With ECOS’s antispam settings turned on, inbox junk is eliminated and employees can focus better on important tasks. Via a policy-based model, ECOS can apply custom settings per organizational unit and per user.
5. Automatic protection
A common admin task is new user enrollment. In ECOS, admins can automatically assign a license to a new user and enable protection via a group policy. In other words, automation of new user mailbox protection saves time and eases management for admins.
Get a free trial of ESET Cloud Office Security here.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which include Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities.
About ESET
For 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint security to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give individuals and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D facilities worldwide, ESET became the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003.

