Turla Crutch attacks Ministry of Foreign Affairs in an EU country, misuses Dropbox in cyber-espionage, ESET discovers
Created: 2020-12-02 10:01:41

BRATISLAVA, MONTREAL – ESET researchers discovered a previously undocumented backdoor and document stealer used for cyber-espionage. ESET has been able to attribute the program, dubbed Crutch by its developers, to the infamous Turla APT group. It was in use from 2015 until at least early 2020. ESET has seen Crutch on the network of a Ministry of Foreign Affairs in a country of the European Union, suggesting that this malware family is only used against very specific targets. These tools were designed to exfiltrate sensitive documents and other files to Dropbox accounts controlled by Turla operators.
“The main malicious activity is exfiltration of documents and other sensitive files. The sophistication of the attacks and technical details of the discovery further strengthen the perception that the Turla group has considerable resources to operate such a large and diverse arsenal,” says Matthieu Faou, an ESET researcher who investigates the Turla APT group. “Furthermore, Crutch is able to bypass some security layers by abusing legitimate infrastructure – here, Dropbox – in order to blend into normal network traffic while exfiltrating stolen documents and receiving commands from its operators.”
In order to have a rough idea of the working hours of the operators, ESET exported those hours at which they uploaded ZIP files to the Dropbox accounts they operate. For this, researchers collected 506 different timestamps ranging from October 2018 to July 2019, as this should show when the operators were working and not when the victims’ machines were active. The operators are likely to operate in the UTC+3 time zone.
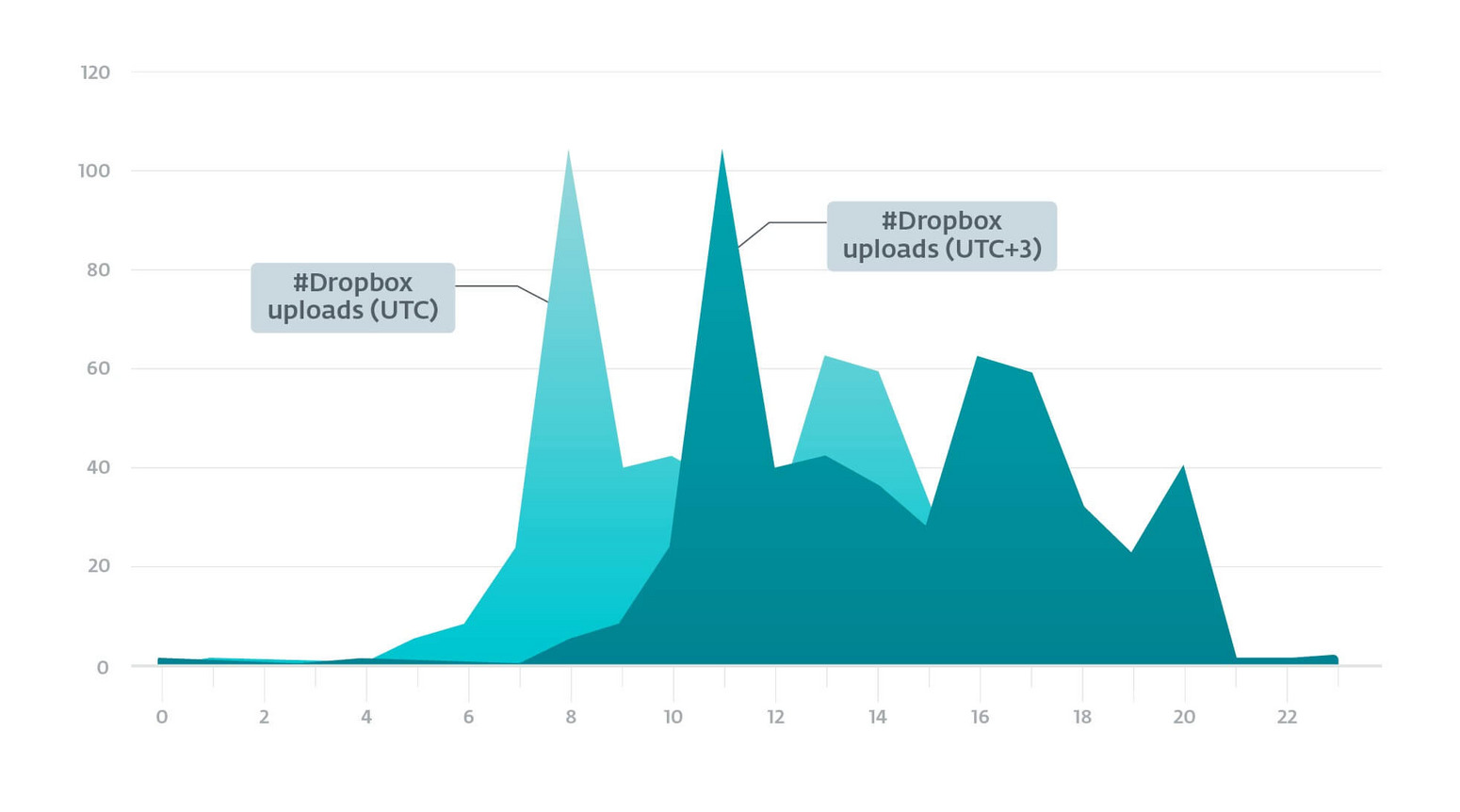
Working hours of Crutch operators based on the uploads to Dropbox zone.
ESET Research was able to identify strong links between a Crutch dropper from 2016 and Gazer. The latter, also known as WhiteBear, is a second-stage backdoor used by Turla in 2016-2017.
Turla has been an active cyber-espionage group for more than 10 years. It has compromised many governments, especially diplomatic entities, all around the world, operating a large malware arsenal that ESET has documentedoverthelast few years.
For more technical details on how Turla Crutch attacks and collects sensitive information, read the blog post Turla Crutch: Keeping the ‘back door’ open on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which include Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities.
About ESET
For 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint security to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give individuals and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D facilities worldwide, ESET became the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003.

