ESET discovers Operation Spalax: Colombian government and industry sector under targeted attack
Created: 2021-01-12 06:50:22
BRATISLAVA, MONTREAL – In 2020, ESET researchers observed several attacks exclusively targeting Colombian entities, which have collectively been dubbed Operation Spalax. These attacks are ongoing and are focused on both government institutions and private companies, especially in the energy and metallurgical industries. The attackers rely on the use of remote access trojans, most likely to conduct cyber-espionage activities.
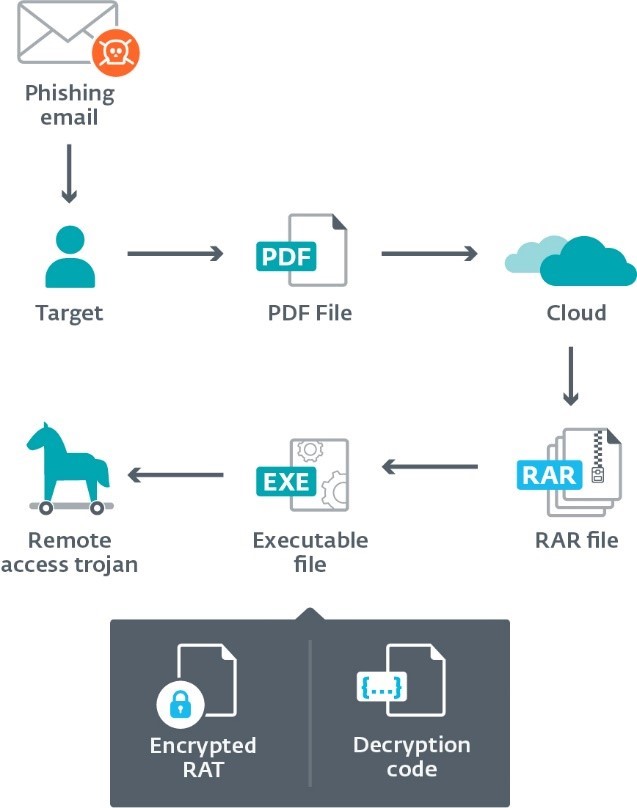
Targets are approached with emails that lead to the download of malicious files. In most cases, these emails have a PDF document attached containing a link that the user must click. The downloaded files are regular RAR archives that have an executable file inside. These archives are hosted in legitimate file hosting services such as OneDrive or MediaFire. The phishing emails can be a notification to take a mandatory COVID-19 test, attend a court hearing, or pay traffic fines, or they may concern the freezing of bank accounts.
The payloads used in Operation Spalax are remote access trojans. These provide several capabilities not only for remote control, but also for spying on targets: keylogging, screen capture, clipboard hijacking, exfiltration of files, and the ability to download and execute other malware, to name a few.
“ESET observed at least 24 different IP addresses in use during the second half of 2020. These are probably compromised devices that act as proxies for their C&C servers. This, combined with the use of dynamic DNS services, means that their infrastructure never stays still. We have seen at least 70 domain names active in this time frame, and they register new ones on a regular basis,” says Matías Porolli, an ESET researcher who investigated Spalax.
Targeted malware attacks against Colombian entities have been scaled up since the campaigns that were described by other researchers last year. The landscape has changed from a campaign with a handful of C&C servers and domain names into a campaign with very large and fast-changing infrastructure with hundreds of domain names used since 2019.
The attacks ESET saw in 2020 share some TTPs with previous reports about groups targeting Colombia, but also differ in many ways, thus making attribution difficult.
For more technical details about Operation Spalax, read the blog post “Operation Spalax: Targeted malware attacks in Colombia” on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which include Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities.
About ESET
For 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint security to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give individuals and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D facilities worldwide, ESET became the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003.

