ESET research into Latin American banking trojans continues: Bold Ousaban steals credentials with obscene images as a decoy
Created: 2021-05-05 09:26:31
BRATISLAVA, PRAGUE – ESET Research continues its regular series into demystifying Latin American banking trojans, this time with a deep dive into Ousaban (aka Javali) malware. According to ESET telemetry, Ousaban is active only in Brazil, although some sources claim it is active in Europe as well. The malware is primarily focused on stealing credentials from financial institutions and, untypical for a Latin American banking trojan, from popular email services too. ESET named this malware family by combining two words – “ousadia”, which means “boldness” in Portuguese, and “banking trojan”, because Ousaban earned its notoriety for boldness from using sexually obscene images as part of its distribution vector.
ESET has been tracking this malware family, while observing signs of active and continuous development, since 2018. The backdoor capabilities of Ousaban are very similar to those of a typical Latin American banking trojan – simulating mouse and keyboard actions and logging keystrokes. Ousaban is also no exception to the typical behavior of Latin American banking trojans in attacking users of financial institutions via overlay windows crafted specifically for the targets. In contrast, however, Ousaban’s targets include several email services, for which it has overlay windows ready as well.
“Ousaban is delivered mainly through phishing emails using a distribution chain that is quite straightforward. The victim is misled into executing an MSI attached to the phishing email. When executed, the MSI launches an embedded JavaScript downloader that downloads a ZIP archive and extracts its contents, consisting chiefly of a legitimate application, an injector and the encrypted Ousaban. Using DLL side-loading, the banking trojan is ultimately decrypted and executed,” explains Jakub Souček, coordinator of the ESET team that investigated Ousaban.
From a technical perspective, Ousaban’s persistence mechanism is also worthy of note. “Ousaban either creates a LNK file or a simple VBS loader in the startup folder, or it modifies the Windows registry Run key,” reveals Souček. “Furthermore, Ousaban protects its executables with binary obfuscators and enlarges most EXE files to approximately 400 MB, likely to evade detection and automated processing.”
For more technical details about Ousaban, read the blogpost Ousaban – Private photo collection hidden in a CABinet on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
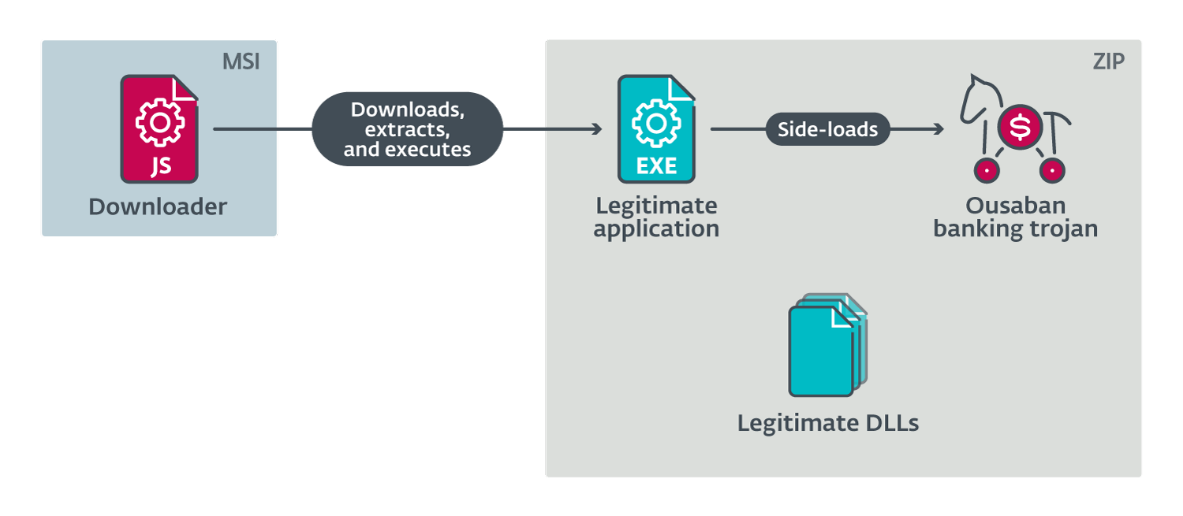
Simple Ousaban distribution chain
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which include Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities.
About ESET
For 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint security to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give individuals and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D facilities worldwide, ESET became the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003.

