ESET Research at RSA Conference 2021: Android stalkerware on the rise
Created: 2021-05-17 10:29:14
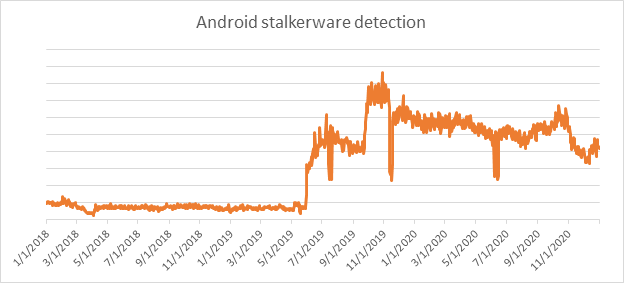
BRATISLAVA – Mobile stalkerware, which is software silently installed by stalkers onto victims’ mobile devices without their knowledge, is on the rise, ESET Research finds. In 2019, ESET telemetry recorded almost five times more Android stalkerware detections than in 2018, and in 2020, almost 1.5 times more were recorded than in 2019. In addition, ESET Research has discovered serious vulnerabilities in Android stalkerware apps and their monitoring servers that could result in serious user impact if exploited. “Security: The Hidden Cost of Android Stalkerware” will be presented today, May 17, 2021, by ESET researcher Lukáš Štefanko from 11:20 to 12:00 PDT (20:20 to 21:00 CEST).
For stalkerware vendors, to stay under the radar and avoid being flagged as stalkerware, their apps are in many cases promoted as providing protection to children, employees, or women, yet the word “spy” is used many times on their websites. “Searching for these tools online isn’t difficult at all; you don’t have to browse underground websites,” explains Štefanko.
ESET researchers manually analyzed 86 stalkerware apps for the Android platform, provided by 86 different vendors. This analysis identified many serious security and privacy issues that could result in a third party – an attacker – taking control of a victim’s device, taking over a stalker’s account, intercepting a victim’s data, framing a victim by uploading fabricated evidence, or achieving remote code execution on a victim’s smartphone. Across 58 of these Android applications, ESET discovered a total of 158 security and privacy issues that can have a serious impact on a victim; indeed, even the stalker or the app’s vendor may be at some risk.
Among the most prevalent issues were insecure transmission of users’ personally identifiable information; storage of sensitive information on external media; exposure of sensitive user information to unauthorized users; server leak of stalkerware client information; and unauthorized data transmission from device to server.
“Following our 90-day coordinated vulnerability disclosure policy, we repeatedly reported these issues to the affected vendors. Unfortunately, to this day, only six vendors have fixed the issues we reported in their apps,” says Štefanko.
For more technical details about ESET’s analysis of Android stalkerware, read the blogpost “Android stalkerware threatens victims further and exposes snoopers themselves” and the white paper “XYZ” on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
Based on our detection telemetry, usage of Android stalkerware is increasing
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which include Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities.
About ESET
For 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint security to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give individuals and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D facilities worldwide, ESET became the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003.

