Cloud-based collaboration and productivity tools are old hat, securing them is new school
Created: 2021-05-31 09:13:55

When a company asks itself whether or not to go off premises with its IT infrastructure, security may not be a top consideration. However, with the massive shift to working from home, and the vast employment of cloud-based collaboration and productivity tools, it should be.
Along with lockdowns and vaccine trials, news of the large-scale hack of the SolarWinds Orion platform and an intrusion campaign targeting IT services companies that ran outdated versions of the Centreon IT monitoring tool sent users a wake-up call early this year. These events drove home the point that cyberthreats are increasingly homing in on cloud-based systems, productivity and collaboration platforms, their users and the IT admins tasked with making it all run smoothly. These are the very means that enable businesses to find efficiencies, focus on core competencies, and ensure business continuity; they are also fast becoming critical points of business security.
While clearly critical, what few IT admins, SOC teams or CISOs may have counted on was the scale of risks unleashed when entire service platforms are targeted by threat actors. In March 2021, a third large-scale disruption reminded business users of cloud services of the vulnerabilities faced by our new productivity and collaboration architecture. If you haven’t guessed, we are discussing the rampant exploitation of Microsoft Exchange, in which ESET researchers identified more than 10 different threat actors or groups that likely leveraged this vulnerability chain, feasting off exposed internet-facing servers and sending shock waves across the IT industry.
New behaviors require new security
If we rewind to the time just prior to the COVID-19 pandemic and look at businesses hunting for security solutions, we’d find that ESET had just introduced ESET Cloud Office Security (ECOS). Bolstering security for Microsoft 365, including OneDrive and Exchange Online, ECOS proved easy to implement and manage for SMB and Enterprise customers alike. Within weeks of its launch, MSPs could also offer ECOS in managed environments, simplifying security provision and reporting for cloud customers via the ECOS dashboard.
As ECOS was put through its paces, the pandemic accelerated the need to overcome issues around productivity costs and business continuity, driving ever more businesses to the cloud. We’ve seen “crowd everything” – from funding to gaming and, of course, business collaboration, all of which have blossomed over the past 15-plus months. Yet, while the pandemic has cemented these as common practices and tools, increasing attention must be paid to securing them.
To that end, ECOS now extends protection to Microsoft Teams and SharePoint Online. This is a big plus for SMBs and others who are operating in the cloud because it hardens protection for business continuity via the very tools that allow distributed work and collaboration.
The protection of organizations from supply-chain attacks as per SolarWinds Orion, intrusions like the Centreon case, or exploitations of internet-facing services like the Microsoft Exchange attacks – impacting thousands of businesses and institutions globally – can be a major challenge to organizations, especially to those ill-prepared. In some of these cases, attackers appear to have infiltrated systems and persisted there for substantial periods of time. These attacks were primarily carried out – at least in the initial stages – by advanced threat actors who command high levels of skills and resources. Simply said, you have to fight your own (network’s) battles, and service providers have to fight theirs.
What ESET Cloud Office Security can do
While the onus of properly configuring and securing the large-scale infrastructure described above lies on both service providers and their clients, it can, does and will impact any and all users of the technology. Endpoint protection, cloud-based or not, will not change the fact that the duty to prevent and mitigate these incidents falls rather heavily on end users as well.
When these incidents do occur, we can expect super blooms of ransomware and other malicious campaigns that seek to leverage the extensive periods of vulnerability and access to impacted networks. As such, if you use the tool, you have signed up for a role in securing your environment; that is the status quo.
While the majority of attacks and disruptions faced by organizations haven’t stemmed from these large-scale events, mitigating the impact largely mirrors more common threats and comes down to addressing the “what can be controlled” in a business’s own environment. Considering the near-universal uptake of productivity tools, a product like ECOS goes a long way in adding immediate protections for the most popular, including Exchange Online, OneDrive, SharePoint Online and Teams.
Spam and malware
For the benefit of IT admins who need to manage protection for 25 seats or more, ECOS delivers an effective multi-tenant and scalable service, protecting all major Microsoft 365 cloud services, such as Exchange Online mailboxes, OneDrive, Teams and SharePoint Online, against malware. On top of that, Exchange Online is also protected against phishing and spam emails.
ESET Cloud Office Security can be managed through a web-based console with user-centric, issue-centric and group-centric views. It also checks all incoming emails delivered to a customer’s Microsoft 365 inbox. Our award-winning antispam technology works as the first layer, filtering out spam messages with near-100% accuracy. The second layer is our malware scanner, which detects malicious or suspicious attachments. The third layer protects against phishing (anti-phishing). Learn more about these features here.
Every file that is uploaded to OneDrive, shared via SharePoint, or transferred via Teams, is checked using our powerful malware detection engine, which leverages the same technology as ESET’s endpoint solutions. If the engine detects a dangerous file, it is placed in quarantine, where it is accessible only by administrators; the user remains protected.
To back that up, admins benefit from ECOS’s easy-to-use cloud console, which gives an overview of quarantined items and immediately notifies them when a detection occurs.
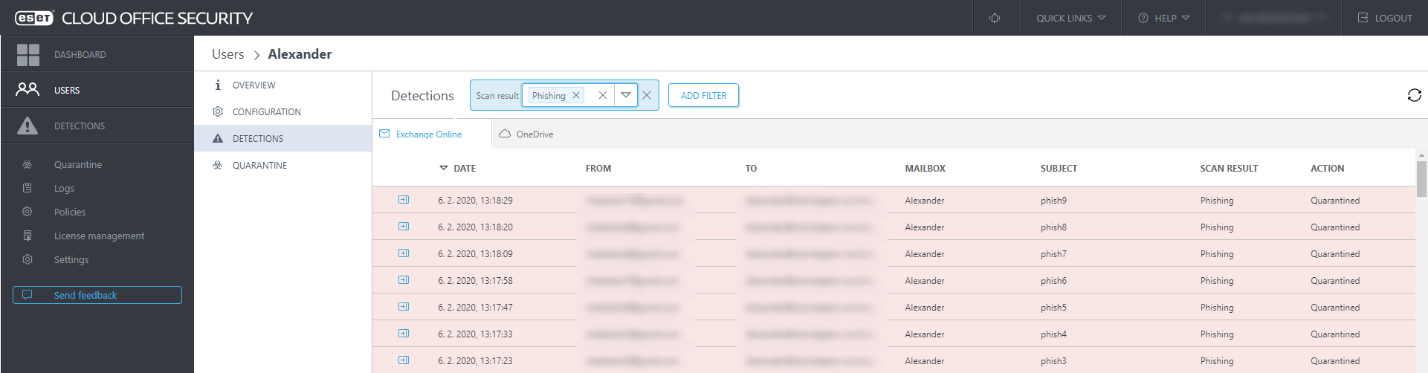
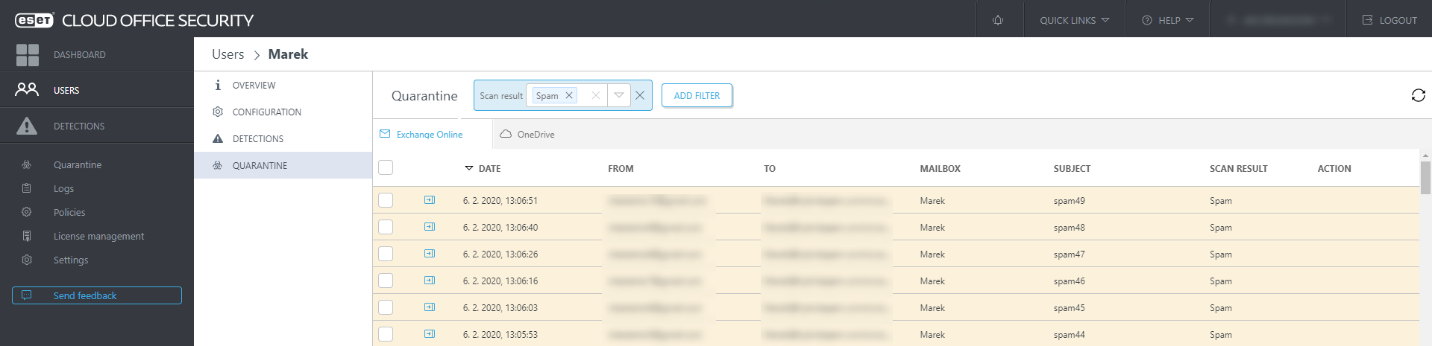
images 1. and 2. ECOS mangement dashboard view of Detections and Quarantined items
Renewing the promise of the cloud?
The large-scale attacks seen in Q1 2021 certainly put a few dents into cloud operations and collaboration platforms; however, one of the main benefits of moving infrastructure to the cloud, and also common to this product, is the ease of initial deployment. ECOS can secure these systems quickly.
In cases where customers have a Microsoft 365 plan, purchase an eligible ECOS license and have an ESET Business Account (for which registration is free) or an ESET MSP Account, it takes an average of five minutes to connect ECOS to a Microsoft 365 environment and initiate protection.
Scaling for maturity of security operations
A major benefit to scalable systems like ECOS is that configuration can be suited to company size and maturity of IT security staff. First, you’ll get your protection, then options to leverage further features.
ECOS ensures admins get a quick overview of what is happening in their company’s instance of Microsoft 365 from a security perspective. It also provides crucial information about the total number of protected users, license usage, those users who are the largest spam, malicious and phishing email recipients, and the top suspicious OneDrive, SharePoint and Teams accounts or groups/sites. This can be viewed over a timescale of 24 hours, 7 days and 30 days. Also provided is a dedicated view for Exchange Online, OneDrive, SharePoint and Teams detections with spam, malware and phishing traffic charts and total numbers of detections.
What has Cloud Office Security seen in its first year?
Many businesses that have onboarded the (now) indispensable productivity tools have done so confident that the inbuilt security provided by Microsoft is sufficient to maintain business continuity, and, more broadly, to keep their systems safe. By Microsoft’s own account, a lot of “us” are on Microsoft 365 and Teams. As of Q3 2020, Microsoft reported 258 million monthly active Microsoft 365 business users, and 75 million daily active Teams users. That’s on top of the 1.2 billion active users of Microsoft Office.
The wide acceptance of these products enables, to a large degree, modern business and governance the world over. Their success also means they are targeted in various ways, from poisoned macros in Word documents sent via Outlook emails to incidents of exploitation of Microsoft Exchange servers. Neither security by design nor Microsoft’s native security have completely stopped these security challenges for users. This is to be expected for such large infrastructure, and for the outsized user numbers.
With cloud-based elements like Microsoft 365, Teams and SharePoint, using these key Microsoft products strongly warrants users adding further security measures. ECOS is cost-effective, easy/rapid to deploy and scalable across the entire range of business and institutional sizes.
ESET’s award-winning engine, the same as used in ESET Mail Security, is used in ECOS to scan all incoming and outgoing emails and attachments in Exchange Online for spam, phishing and malware. Read more about ECOS’s protection against threats vectoring from email here:
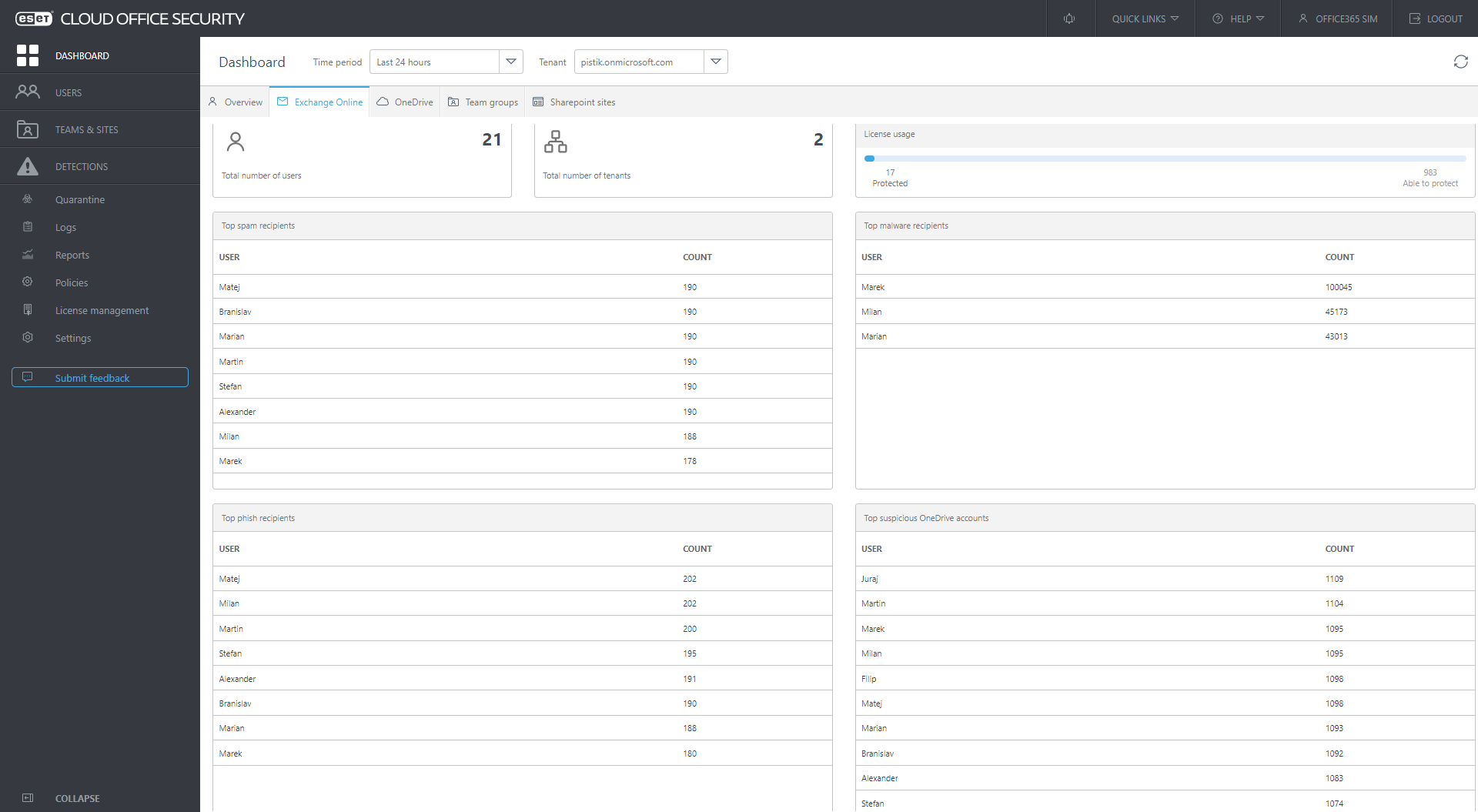
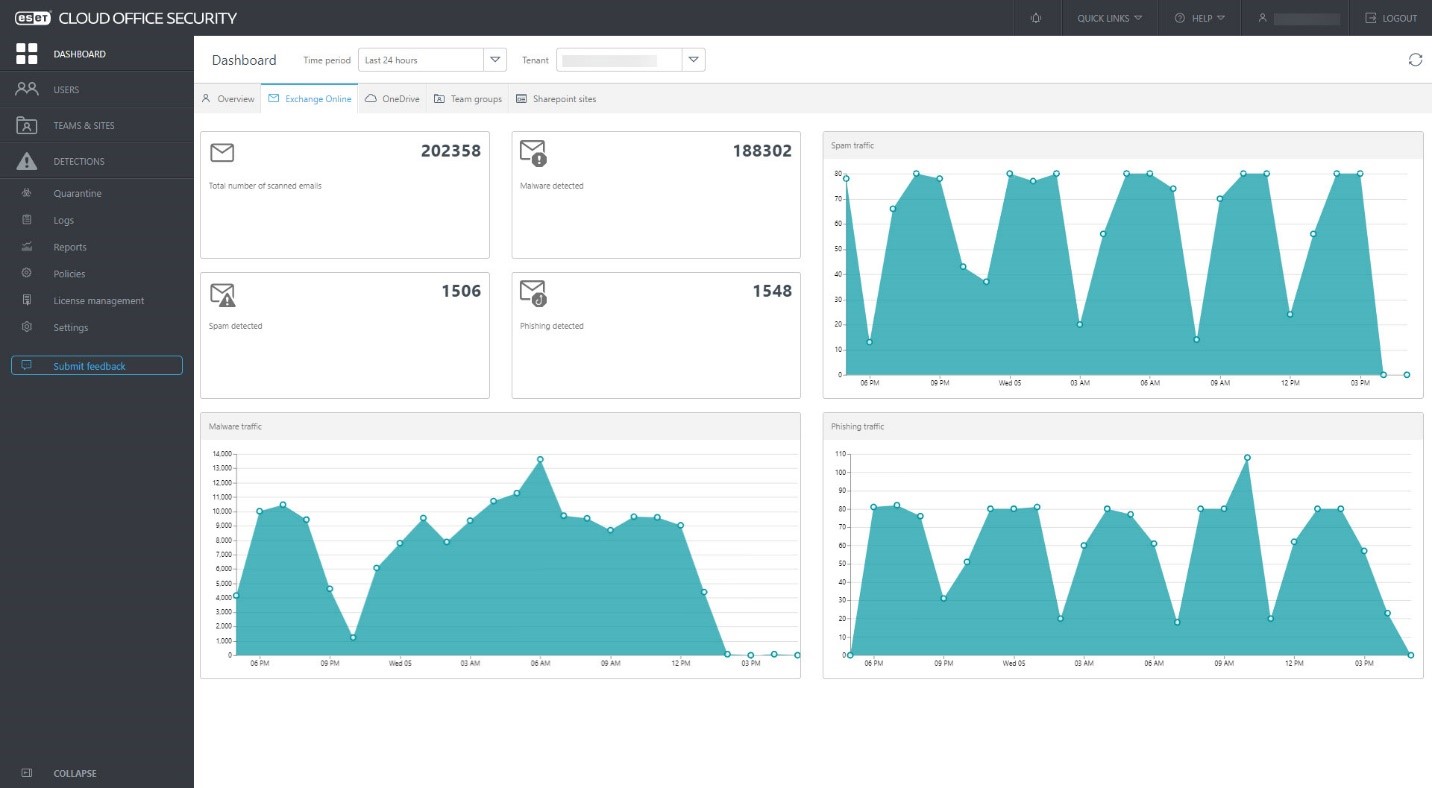
images 3-6. ECOS Dashboard views for: Exchange, OneDrive, Teams, SharePoint
In 2021, via the ECOS’s many dashboards, IT Admins and SOC Teams alike were able to see threats – significant threat types that slipped by Microsoft’s native security:
1. HTML/Fraud: A detection name covering a diversity of HTML-based content, distributed with the aim of gaining money or other profit from the victim’s involvement. This includes scam websites, as well as HMTL-based emails and email attachments.
2. HTML/Phishing.Agent: A detection name for malicious HTML code often used in a phishing email’s attachment. When such an attachment is opened, a phishing site is opened in the web browser, posing as an official banking, payment service or social networking website. The website requests credentials or other sensitive information, which is then sent to the attacker.
3. DOC/Fraud: A detection name mainly covering Microsoft Word documents with various types of fraudulent content, primarily distributed via email. The goal of this threat is to profit from the victim’s involvement, often by persuading the disclosure of online account credentials or sensitive data. Documents often contain links to websites where victims are asked to fill in personal data.
While malicious documents vectoring from email and poisoned websites still comprise the largest proportion of threats to business ecosystems, we shouldn’t forget these also track to newer SharePoint-based features that mushroomed in popularity under COVID-19. These files can and do make their way to SharePoint.
Company culture and IT administrator settings are critical here. Adding a layer to securing collaboration platforms is essential because part of productivity entails speed. Users’ caution or attention may flag when working within Teams or SharePoint, which raises the risk of compromised documents making it into your environment.
To find out more, or to get a free trial of ESET Cloud Office Security, read more here.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which include Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities.
About ESET
For 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint security to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give individuals and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D facilities worldwide, ESET became the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003.

