What is the Zero Trust security model, and why is its adoption growing?
Created: 2021-07-08 07:54:35
Zero Trust promotes the concept that organizations should not trust any entity inside or outside their network perimeters in a predetermined fashion.
Adoption of the Zero Trust security model is picking up steam at last. In February 2020 – before the pandemic swept the world – a survey of more than 400 IT security decision makers conducted by Cybersecurity Insiders and Pulse Secure revealed that 72% of organizations were planning to either assess or implement Zero Trust in their security strategy during the course of the year. Then, in May 2021, President Biden’s Executive Order on Improving the Nation’s Cybersecurity threw down the gauntlet by acknowledging the broken state of the US’s federal model of cybersecurity and the need to implement a Zero Trust Architecture.
In this article, we briefly explain Zero Trust, what is needed to implement it, and why interest in it is growing.
What is Zero Trust?
According to Forrester, which created this concept back in 2010, in contrast to the traditional, perimeter-based security model that builds on the premise of “trust but verify,” Zero Trust says organizations should never trust any entity, whether internal or external. In other words, “never trust, always verify.” The Zero Trust model builds security around each of the key resources and entities of an organization: data, networks, devices, workloads, and people.
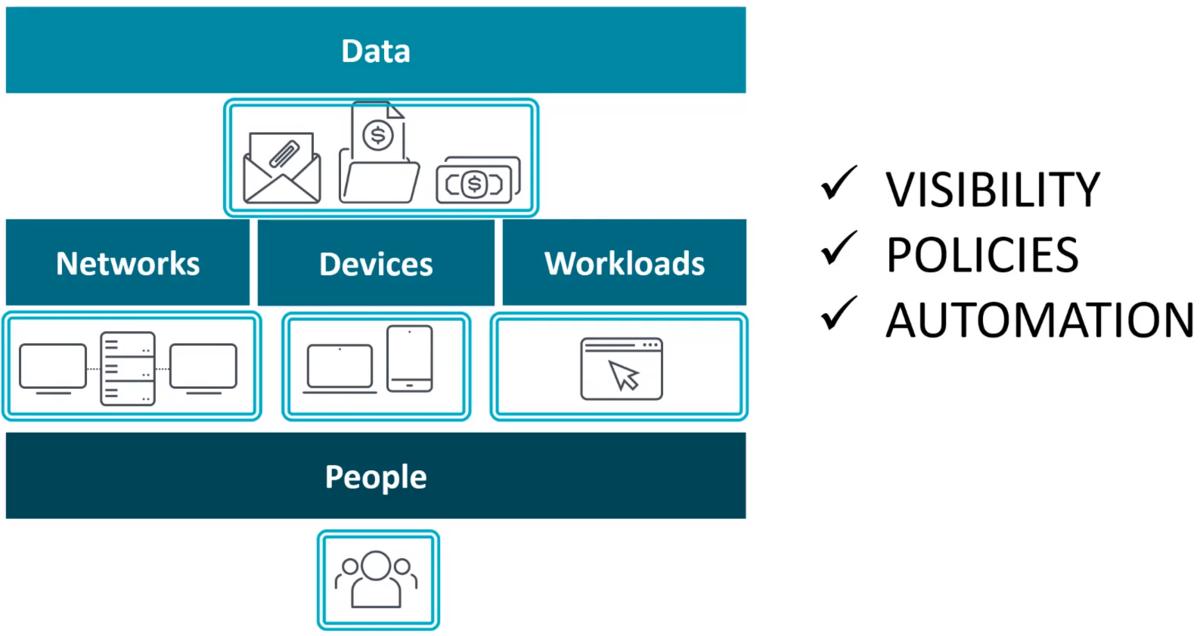
Figure 1 – The Zero Trust model builds security around each of the key resources of an organization.
In the traditional IT security model, the security posture of an organization should be like a castle guarded by a moat, which represents the network. In such a setup, it is difficult to gain access to an organization’s resources from outside the network. At the same time, everyone who is inside the network is considered trusted by default. The problem with this approach, however, is that once an attacker gains access to the network, and thereby becomes trusted by default, all the organization’s resources are ripe for the picking.
In contrast, the Zero Trust model assumes that attackers are inside the network just as much as outside. For this reason, trust cannot be given indiscriminately to users and devices by default.
 Figure 2 – Animated graphic that exemplifies the traditional perimeter-based security model
Figure 2 – Animated graphic that exemplifies the traditional perimeter-based security model
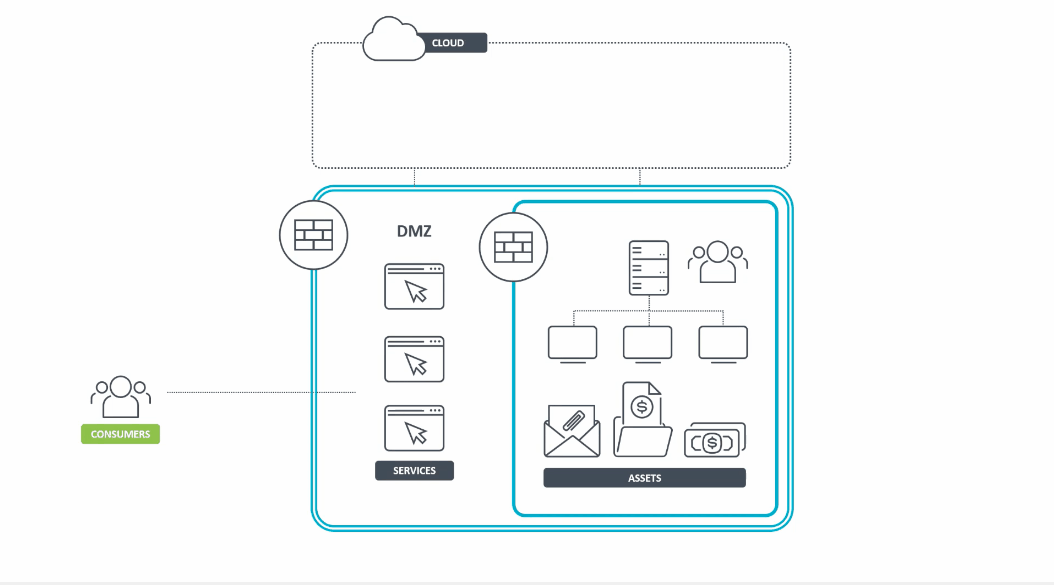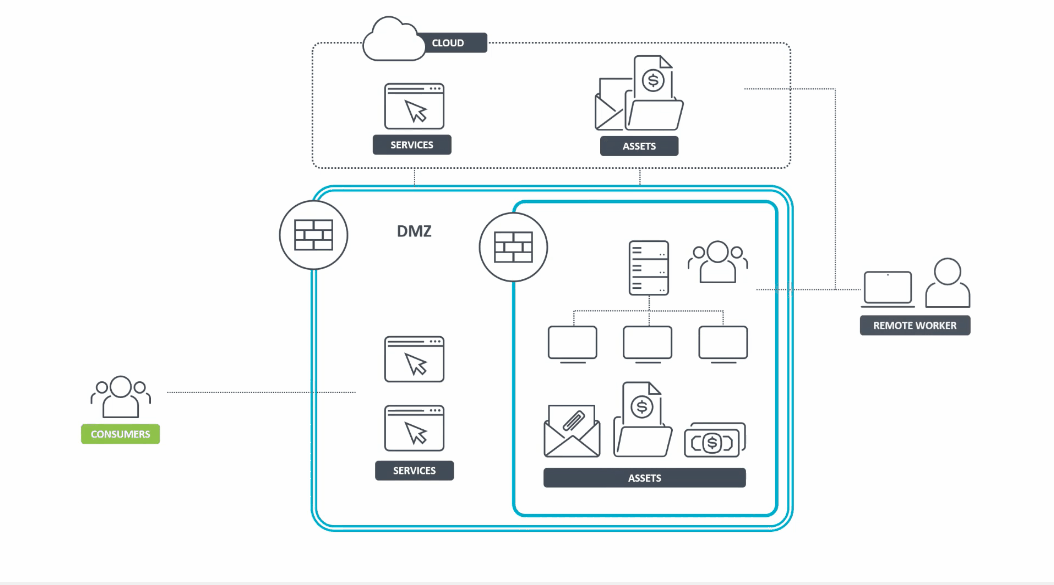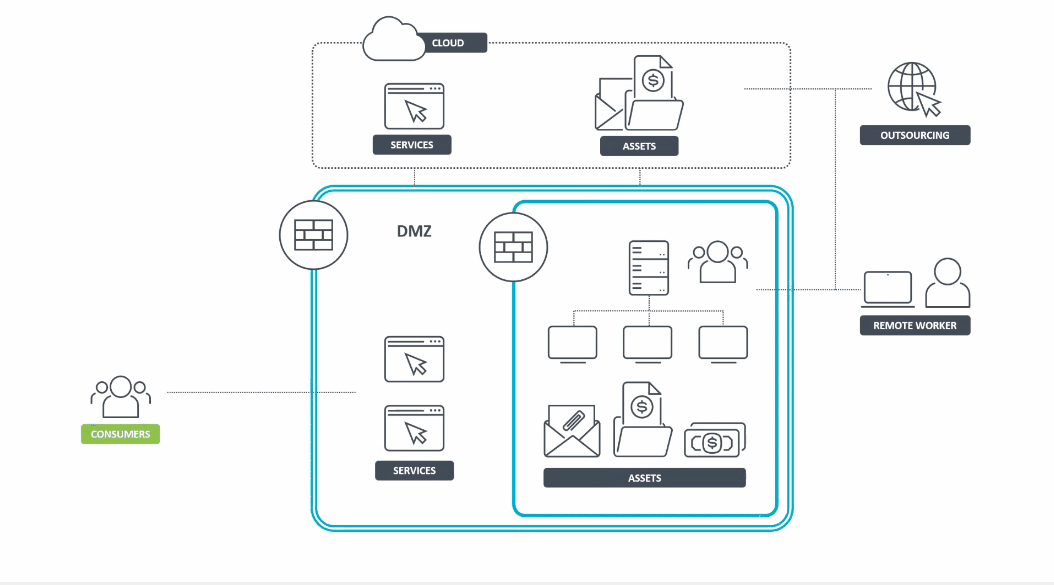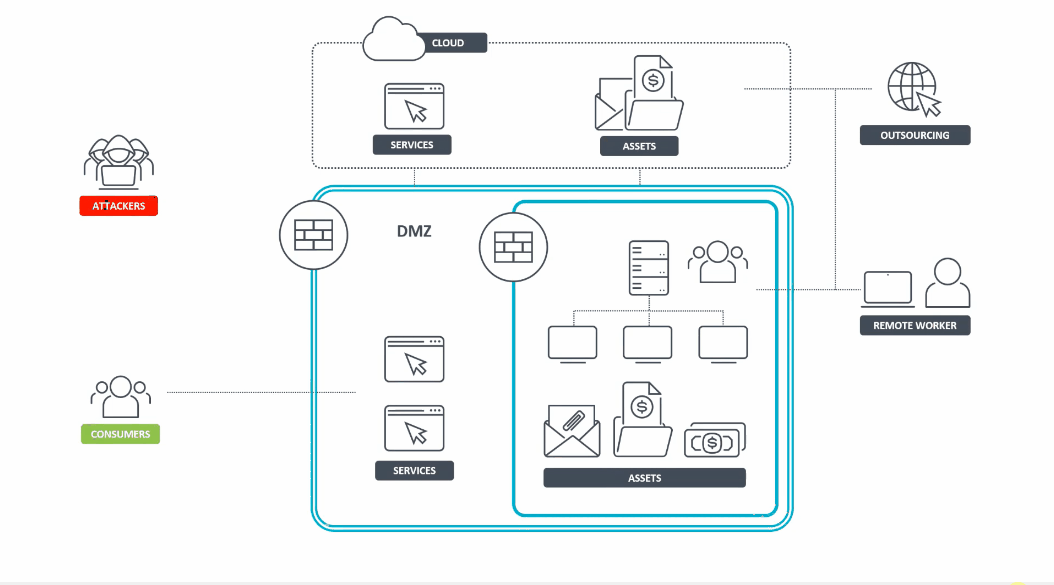
Figure 3 – Animated graphic that exemplifies the Zero Trust security model
What does an organization need to do to implement the Zero Trust model?
There are three core areas of capability that an organization should develop as it implements the Zero Trust model:
- Visibility: Identify devices and resources that should be monitored and protected. It is not possible to protect a resource that you do not know about. Having visibility into all your resources and access points is indispensable.
- Policies: Establish controls that only permit specific people to have access to specific resources under specific conditions. In other words, a granular level of policy controls is required.
- Automation: Automate processes to ensure the correct application of policies and enable the organization to rapidly adapt to any deviations from standard procedures.
Building on the foundational capabilities outlined here, we can define Zero Trust as a security model that builds defenses around each of the following entities: data, networks, devices, workloads, and people.
What is driving the renewed interest in and adoption of the Zero Trust model?
With a Zero Trust environment, not only do you have control and knowledge of all your data (all the time), but in the event of a security breach, you can quickly detect when and where attackers may have pilfered your data, as Forrester explains. Considering that the 2020 Cost of a Data Breach Report by IBM and the Ponemon Institute revealed the average cost of a data breach globally to be US$3.86 million and the average time to identify and contain a breach 280 days, the Zero Trust model appears rather attractive.
On the other hand, with the continued growth of the bring your own device (BYOD) and remote work phenomena, more and more employees need to have access to their organization’s internal resources from any place at any time. It is worth highlighting that the pandemic saw a gigantic increase in brute-force attack attempts against the remote desktop protocol (RDP), demonstrating the high interest of cybercriminals in taking advantage of the current remote work situation.
Another component driving Zero Trust is the growing adoption and use of storage services in the cloud. The cloud often hosts the data, resources, and even the critical services of organizations.
Other vectors that have proven fatal for the perimeter-based security model are supply-chain attacks – as was the case with NoxPlayer, an Android emulator used by gamers to play mobile games on their PCs and Macs – outsourcing of services, and employee turnover, among others.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which include Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities.
About ESET
For 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint security to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give individuals and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D facilities worldwide, ESET became the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003.

