When printing got dangerous: The PrintNightmare
Created: 2021-07-14 08:32:07
ESET offers product configuration tips to keep you safe from PrintNightmare exploits while retaining functional network printing
Patches for Windows Print Spooler are out, yet problems seem to persist.
As news trickles out about the recent out-of-band security patch for the Windows Print Spooler service seemingly causing printing issues, Microsoft is rolling back fixes from the June 2021 cumulative update preview, which is apparently the real source of the printing problems rather than the out-of-band patch for PrintNightmare (aka CVE-2021-34527 / CVE-2021-1675).
Unrelated to the printing problems, researchers pointed out that the patch, which aims to address the PrintNightmare vulnerability, fails to do the job fully, although it limits the range of possible attacks.
While Microsoft feels confident that the update is working as designed, some researchers in the security community suggest otherwise. The wrangle seems to be over the source of the problem, whether it is the insecure configuration of a few registry settings or forgetting to check an alternative format for the path to an attacker’s malicious DLL.
The issue is severe enough that an emergency directive from the Cybersecurity and Infrastructure Security Agency (CISA) has ordered federal agencies to mitigate the actively exploited Window Print Spooler vulnerability on their networks.
Keep safe and keep on printing
In case you can’t make use of the patches — and even if you can, at least until the patches are sufficient — ESET is releasing a few product configuration tips that help prevent PrintNightmare exploits from compromising your systems. Microsoft’s workaround advice is to disable the print spooler service entirely, or to disable remote printing via group policies. The first option disables all printing on that device, to both local and remote printers, while the second leaves local printing enabled but disables remote printing to the local printer. Applied across your whole network, either workaround disables all remote printing.
However, a less drastic approach is to set up rules in ESET Endpoint Security, or via policies from ESET PROTECT, that block malicious use of the Print Spooler service. Using ESET’s Host-Based Intrusion Prevention System (HIPS) layer, IT admins can block spoolsv.exe from writing new DLLs to the driver folder (a necessary element of remote exploitation of the PrintNightmare vulnerability) following these steps:
1. Open the main program window of your ESET Windows product.
2. Press the F5 key to access Advanced setup.
3. Click Detection Engine > HIPS.
4. Scroll down.
5. Click Edit to access HIPS rules.
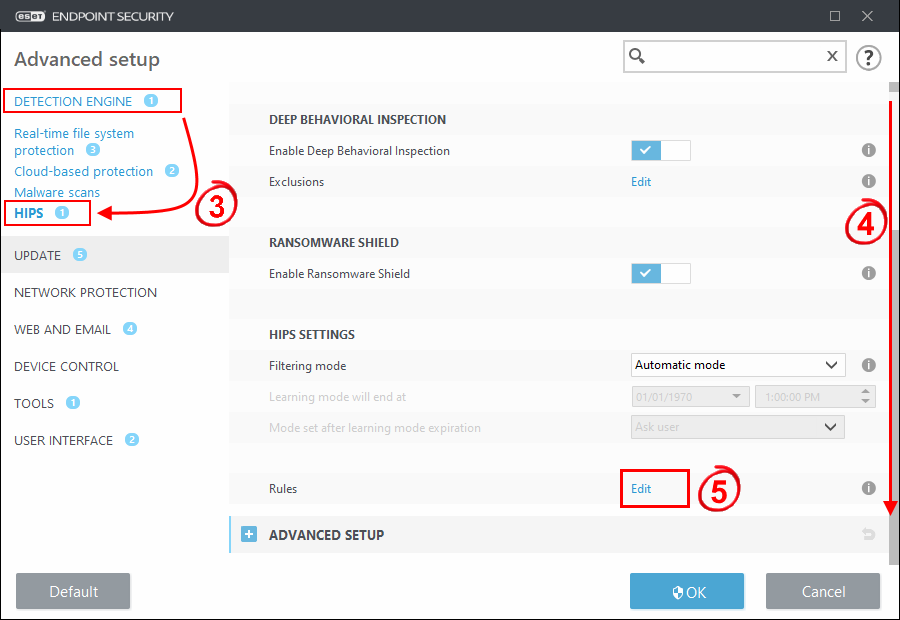
6. Click Add.
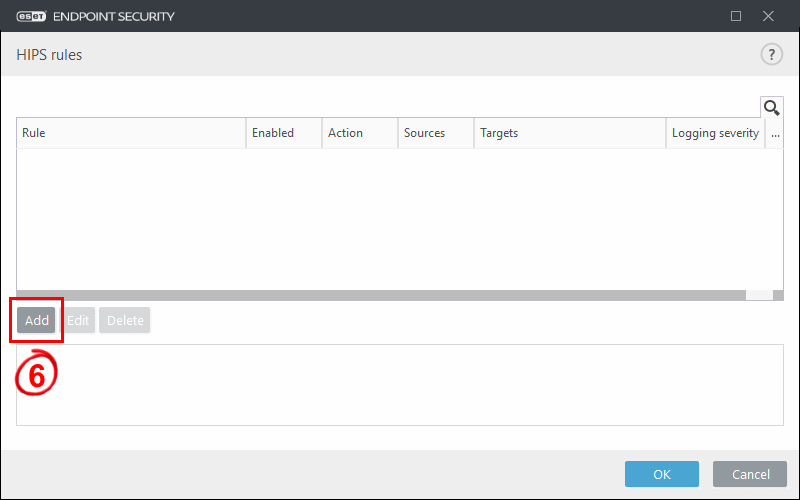
7. Configure a new rule. In the HIPS rule settings window, you can name the rule “Disallow spoolsv.exe DLL writing.” Then block operations affecting target files (both specified in subsequent steps), and enable the rule, logging of information about this rule, and notifying the user with a small pop-up window. When you are finished, click Next.
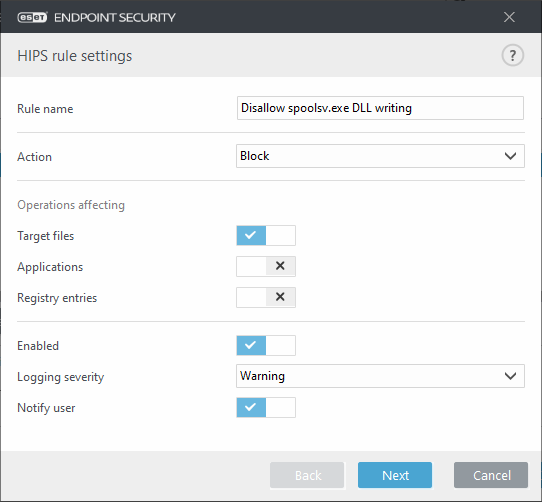
8. In the Source applications window, select Specific applications from the drop-down menu and then click Add.
9. In the Add window, type the following file path, click OK and then Add (note the file path is based on a system with Windows installed in C:\Windows; alter as necessary).
· C:\Windows\System32\spoolsv.exe
10. Click Next.
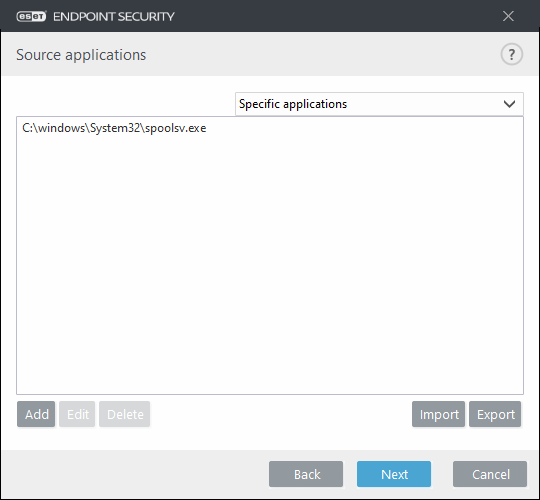
11. Click the slider bar next to Write to file and then click Next.
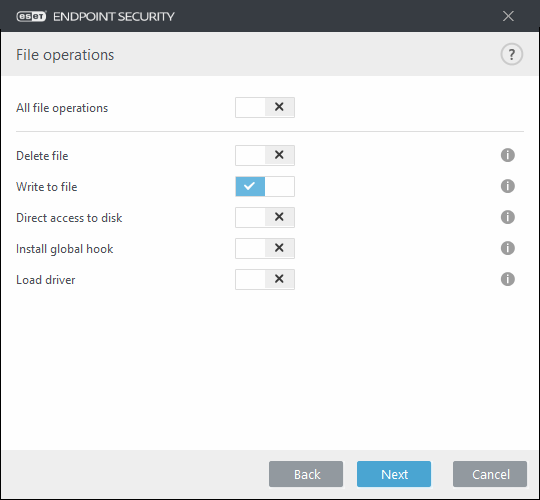
12. In the Target files window, select Specific files from the drop-down menu and then click Add.
13. In the Add window, type the following file path, click OK and then Add.
· C:\Windows\System32\spool\drivers\*
14. Click Finish.
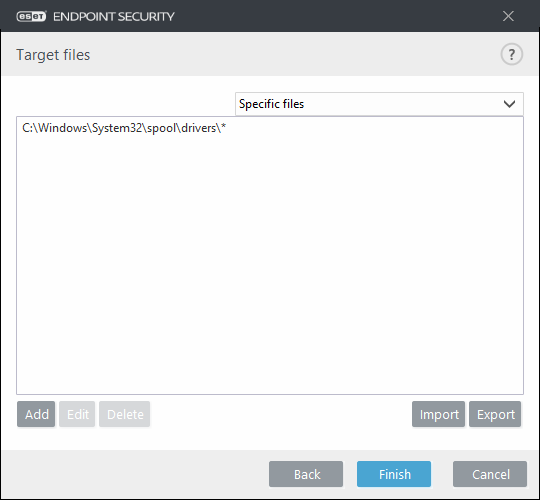
15. Once completed the new rule should look like this:
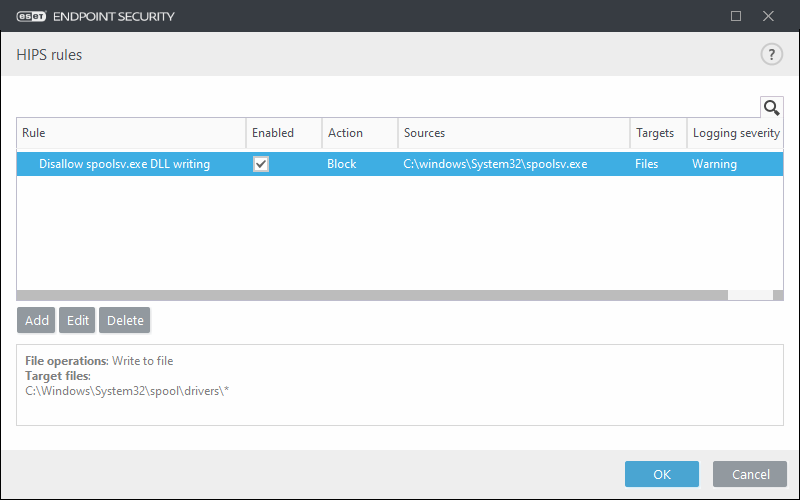
16. Click OK twice to return to the main program window and enable the new rule.
Once enabled, this HIPS rule should leave all local and remote printing functionality intact (that is, printing to local and remote printers, and accepting remotely submitted print jobs to a local printer) except that installing new printers will fail:
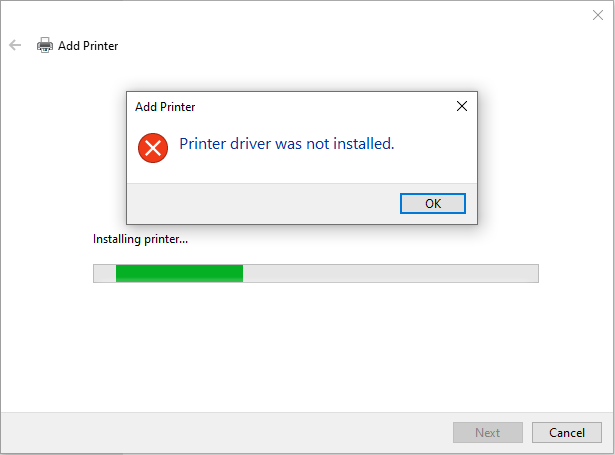
Printers that are already installed should remain functional. If this HIPS rule has been deployed, a new printer can be installed or configured on a workstation by temporarily disabling this rule and enabling it once the printer is installed.
Although ESET researchers have tested this rule, if printing is a critical function in your business you should test it carefully in your environment before deploying it widely.
Finally, it is important to remember to disable this rule once fully functional patches are released by Microsoft and have been installed in your environment.
We thank ESET Netherlands CTO Donny Maasland and his team for this suggestion, and for the next. For those who use ESET Enterprise Inspector — ESET’s endpoint detection and response solution — you can create custom rules that detect exploitation of CVE-2021-1675:
- PrintNightmare — Printer Spooler dropped .dll file [K1989A], which detects spoolsv.exe dropping a DLL file with a low reputation into the spool drivers folder.
- PrintNightmare — Printer Spooler loaded untrusted DLL [K1989B], which detects spoolsv.exe loading a DLL file with a low reputation from the spool drivers folder.
- PrintNightmare — Printer Spooler executed cmd.exe [K1989C], which detects spoolsv.exe spawning cmd.exe as a child process.
While the rules referenced here are configured for ESET Enterprise Inspector, it should be possible to adapt them to other endpoint detection and response platforms.
In addition, you can keep track of the rapidly evolving situation around PrintNightmare on ESET’s support page here.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which include Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities.
About ESET
For 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint security to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give individuals and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D facilities worldwide, ESET became the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003.

