Android/FakeAdBlocker misuses URL shortener services and iOS calendars, and distributes trojans to Android devices
Created: 2021-07-20 08:36:46
BRATISLAVA, KOŠICE — July 20, 2021 — ESET Research has analyzed an aggressive advertising-based threat — Android/FakeAdBlocker — which downloads malicious payloads provided by its operator’s command and control server. Android/FakeAdBlocker usually hides its launcher icon after initial launch, delivers unwanted scareware or adult content advertisements, and creates spam events for upcoming months in iOS and Android calendars. These ads often cost their victims money by sending premium rate SMS messages, subscribing to unnecessary services, or downloading Android banking trojans, SMS trojans and malicious applications. Additionally, the malware uses URL shortener services to create links to ads, which in some cases monetize their clicks.
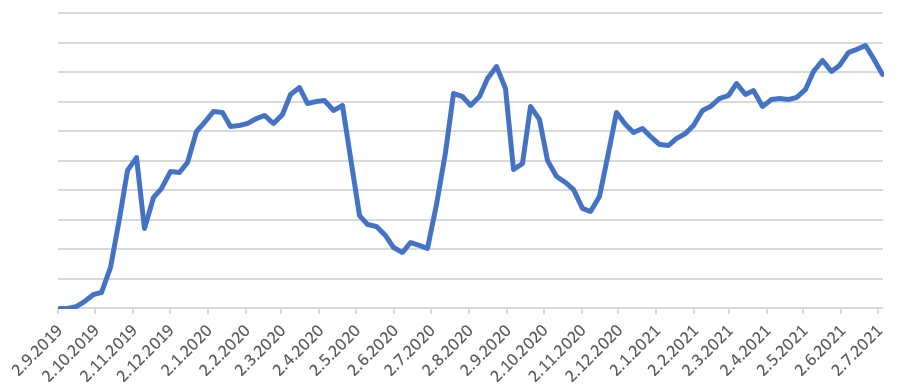
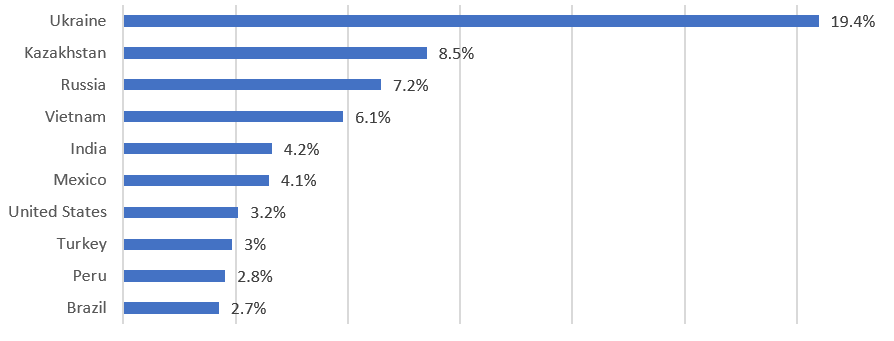
Based on ESET telemetry, Android/FakeAdBlocker was spotted for the first time in September 2019, and from January 1 to July 1, 2021, more than 150,000 instances of this threat were downloaded to Android devices. The most affected countries are Ukraine, Kazakhstan, Russia, Vietnam, India, Mexico, and the United States. Although in most cases the malware displays aggressive ads, ESET has identified hundreds of cases in which different malicious payloads were downloaded and executed, including the Cerberus banking trojan, which was variously disguised as Chrome, Android Update, Adobe Flash Player, or Update Android, and downloaded to devices in Turkey, Poland, Spain, Greece, and Italy. ESET also saw the Ginp trojan being downloaded in Greece and the Middle East.
“Based on our telemetry, it appears that many users tend to download Android apps from outside Google Play, which might lead them to download malicious apps delivered through aggressive advertising practices that are used to generate revenue for their authors,” explains ESET researcher Lukáš Štefanko, who analyzed Android/FakeAdBlocker. Commenting on the monetization of the shortened URL links, Štefanko adds, “When someone clicks on such a link, an advertisement will be displayed that will generate revenue for the person who generated the shortened URL. The problem is that some of these link shortener services use aggressive advertising techniques such as scareware ads informing users their devices are infected with dangerous malware.”
ESET Research has identified link shortener services pushing events to iOS calendars and distributing the Android/FakeAdBlocker malware that can be launched on Android devices. On iOS devices, besides flooding victims with unwanted ads, these links can create events in victims’ calendars by automatically downloading an ICS calendar file.
“It creates 18 events happening every day, each of which lasts 10 minutes,” says Štefanko. “Their names and descriptions suggest that the victim’s smartphone is infected, the victim’s data is exposed online, or a virus protection app has expired. Descriptions of each event include a link that leads the victim to visit a scareware advertisement website. That website again claims the device has been infected and offers the user an option to download shady cleaner applications from Google Play.”
For victims using Android devices, the situation is more dangerous because these scam websites may provide a malicious app to download from outside the Google Play store. In one scenario, the website requests to download an application called “adBLOCK,” which has nothing to do with the legitimate application and indeed does the opposite of blocking ads. In another scenario, when the victims proceed to download the requested file, they are shown a web page describing the steps to download and install a malicious application with the name “Your File Is Ready To Download.” In both scenarios, a scareware advertisement, or the Android/FakeAdBlocker trojan, is delivered via a URL shortener service.
For more technical details, and to learn how to uninstall Android/FakeAdBlocker, read the blog post “Some URL shortener services distribute Android malware, including banking or SMS trojans” on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
ESET detection telemetry for Android/FakeAdBlocker
Top 10 countries with Android/FakeAdBlocker detections (January 1, 2021 – June 1, 2021)
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which include Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities.
About ESET
For 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint security to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give individuals and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D facilities worldwide, ESET became the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003.

