ESET Research: Ukraine hit by destructive attacks before and during the Russian invasion with HermeticWiper and IsaacWiper
Created: 2022-03-01 07:46:24
A second wiping attack via IsaacWiper started shortly after the Russian military invasion and hit a Ukrainian governmental network
- On February 23, a destructive campaign using HermeticWiper (along with HermeticWizard and HermeticRansom) targeted multiple Ukrainian organizations. This cyberattack preceded the start of the Russian invasion of Ukraine by a few hours.
- HermeticWiper wipes itself from disk by overwriting its own file with random bytes. This anti-forensic measure is likely intended to prevent the analysis of the wiper in a post-incident analysis.
- HermeticWiper is propagated inside compromised local networks by a custom worm we named HermeticWizard.
- On February 24, a second destructive attack against a Ukrainian governmental network started, using a wiper ESET has named IsaacWiper.
- On February 25, attackers dropped a new version of IsaacWiper with debug logs, which may indicate they were unable to wipe some of the targeted machines.
- Malware artifacts suggest that the attacks had been planned for several months.
- ESET Research has not yet been able to attribute these attacks to a known threat actor.
BRATISLAVA — March 1, 2022 — As the Russian invasion was starting in Ukraine, ESET researchers discovered two new wiper malware families targeting Ukrainian organizations. The first cyberattack started a few hours prior to the Russian military invasion as ESET Research reported on its Twitter account, and after the distributed denial-of-service (DDoS) attacks against major Ukrainian websites earlier that day. These destructive attacks leveraged at least three components: HermeticWiper for wiping the data, HermeticWizard for spreading on the local network, and HermeticRansom acting as a decoy ransomware. Malware artifacts suggest that the attacks had been planned for several months. As the Russian invasion started, a second destructive attack against a Ukrainian governmental network started, using a wiper that ESET Research has named IsaacWiper.
“With regard to IsaacWiper, we are currently assessing its links, if any, with HermeticWiper. It is important to note that it was seen in a Ukrainian governmental organization that was not affected by HermeticWiper,” says ESET Head of Threat Research Jean-Ian Boutin.
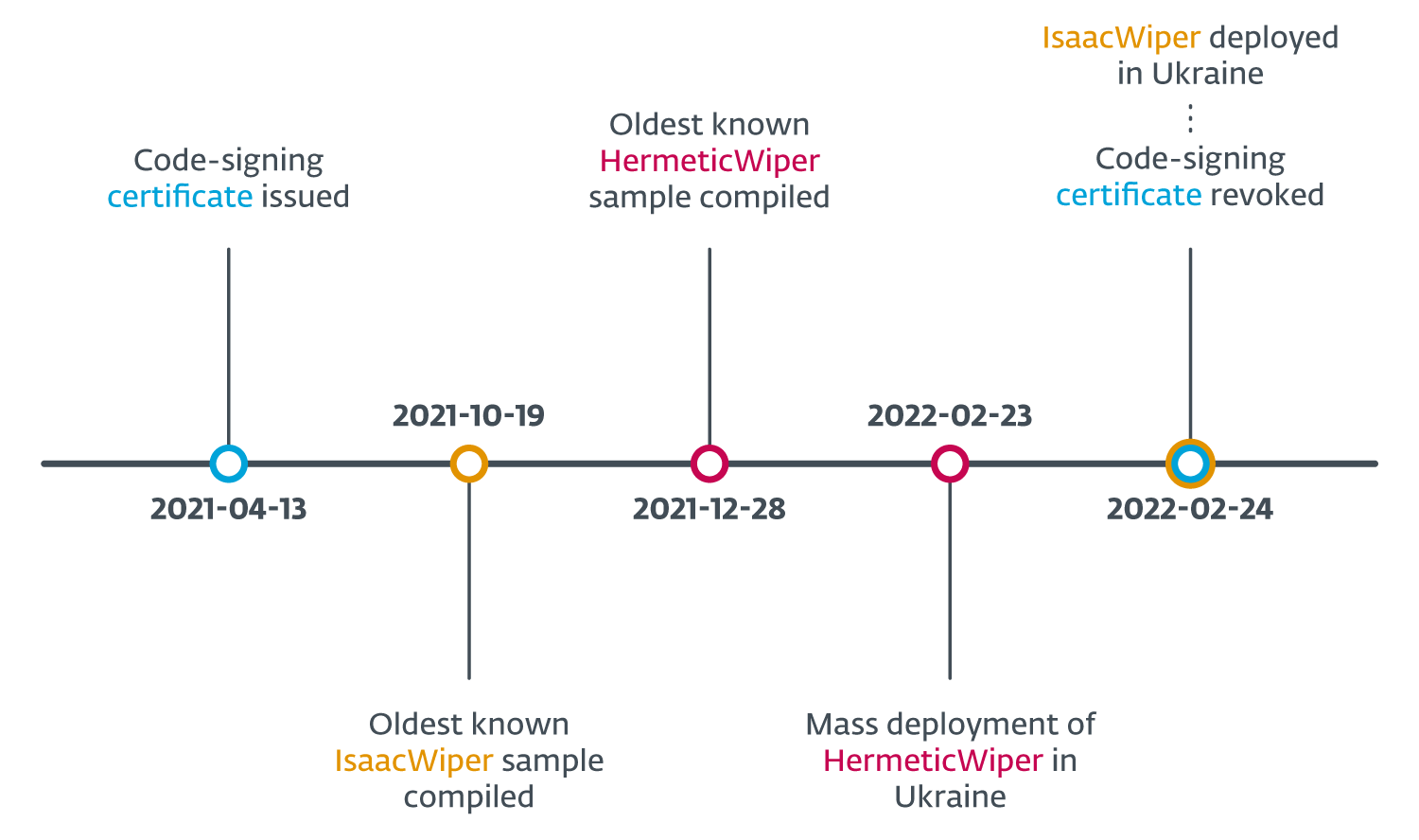
ESET researchers assess with high confidence that the affected organizations were compromised well in advance of the wiper’s deployment. “This is based on several facts: the HermeticWiper PE compilation timestamps, the oldest being December 28, 2021; the code-signing certificate issue date of April 13, 2021; and the deployment of HermeticWiper through the default domain policy in at least one instance, suggesting the attackers had prior access to one of that victim’s Active Directory servers,” says Boutin.
IsaacWiper appeared in ESET telemetry on February 24. The oldest PE compilation timestamp found was October 19, 2021, meaning that if its PE compilation timestamp was not tampered with, IsaacWiper might have been used in previous operations months earlier.
In the case of HermeticWiper, ESET has observed artifacts of lateral movement inside the targeted organizations and that the attackers likely took control of an Active Directory server. A custom worm that ESET researchers named HermeticWizard was used to spread the wiper across the compromised networks. For the second wiper – IsaacWiper – the attackers used RemCom, a remote access tool, and possibly Impacket for movement inside the network.
Furthermore, HermeticWiper wipes itself from disk by overwriting its own file with random bytes. This anti-forensic measure is likely intended to prevent the analysis of the wiper in a post-incident analysis. The decoy ransomware HermeticRansom was deployed at the same time as HermeticWiper, potentially in order to hide the wiper’s actions.
Just a day after the deployment of IsaacWiper, attackers dropped a new version with debug logs. This may indicate that the attackers were unable to wipe some of the targeted machines and added log messages to understand what was happening.
ESET Research has not yet been able to attribute these attacks to a known threat actor due to the lack of any significant code similarity with other samples in the ESET malware collection.
The term “Hermetic” is derived from Hermetica Digital Ltd, a Cypriot company to which the code-signing certificate was issued. According to a report by Reuters, it seems that this certificate was not stolen from Hermetica Digital. Instead, it is likely that the attackers impersonated the Cypriot company in order to get this certificate from DigiCert. ESET Research requested the issuing company DigiCert to revoke the certificate immediately.
For more technical information, read the blogpost on WeLiveSecurity and follow ESET Research on Twitter for the latest news from ESET Research.
Timeline of important events
About ESET
ESET develops software solutions that deliver instant, comprehensive protection against evolving computer security threats. ESET pioneered and continues to lead the industry in proactive threat detection. ESET NOD32 Antivirus, its flagship product, consistently achieves the highest accolades in all types of comparative testing and is the foundational product that builds out the ESET product line to include ESET Smart Security. ESET Smart Security is an integrated antivirus, antispyware, antispam and personal firewall solution that combines accuracy, speed and an extremely small system footprint to create the most effective security solution in the industry. Both products have an extremely efficient code base that eliminates the unnecessary large size found in some solutions. This means faster scanning that doesn’t slow down computers or networks. Sold in more than 160 countries, ESET has worldwide production headquarters in Bratislava, SK and worldwide distribution headquarters in San Diego, U.S. ESET also has offices in Bristol, U.K.; Buenos Aires, AR; Prague, CZ; and is globally represented by an extensive partner network. For more information, visit our local office at https://eset.version-2.sg.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The Company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which includes Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities. For more information, please visit https://www.version-2.com.sg/ or call (65) 6296-4268.

