ESET Research discovers scheme to steal cryptocurrency from Android and iPhone users
Created: 2022-03-24 07:20:12
- This sophisticated malicious cryptocurrency scheme targets mobile devices using Android or iOS operating systems (iPhones).
- The malicious apps were distributed through fake websites, mimicking legitimate wallet services and promoted with ads placed on legitimate sites using misleading articles, and via Telegram and Facebook groups.
- The main goal of this scheme is to steal cryptocurrency funds, especially those of Chinese users.
- ESET Research discovered over 40 copycat websites of popular cryptocurrency wallets and believes that it is likely the work of a criminal group.
- The malicious app behaves differently depending on the operating system it is installed on.
- With cryptocurrencies gaining popularity and the apparent leak of the source code of this threat, ESET expects these techniques to spread to other markets.
BRATISLAVA, KOŠICE — March 24, 2022 — ESET Research discovered and backtracked a sophisticated malicious cryptocurrency scheme that targets mobile devices using Android or iOS operating systems (iPhones). Malicious apps are distributed through fake websites, mimicking legitimate wallet services such as Metamask, Coinbase, Trust Wallet, TokenPocket, Bitpie, imToken, and OneKey. These fake websites are promoted with ads placed on legitimate sites using misleading articles. Furthermore, the threat actors are recruiting intermediaries through Telegram and Facebook groups to further distribute this malicious scheme. The main goal of the malicious apps is to steal users’ funds and until now ESET Research has seen this scheme mainly targeting Chinese users. As cryptocurrencies are gaining popularity, ESET expects these techniques to spread to other markets.
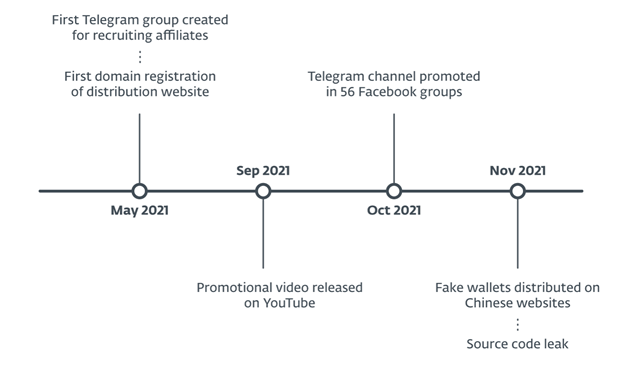
Starting in May 2021, our research uncovered dozens of trojanized cryptocurrency wallet apps. This is a sophisticated attack vector since the malware’s author carried out an in-depth analysis of the legitimate applications misused in this scheme, enabling the insertion of their own malicious code into places where it would be hard to detect while also making sure that such crafted apps had the same functionality as the originals. At this point, ESET Research believes that this is likely the work of one criminal group.
“These malicious apps also represent another threat to victims, as some of them send secret victim seed phrases to the attackers’ server using an unsecured HTTP connection. This means that victims’ funds could be stolen not only by the operator of this scheme, but also by a different attacker eavesdropping on the same network,” says Lukáš Štefanko, ESET researcher who discovered the scheme. “We also discovered 13 malicious apps impersonating the Jaxx Liberty wallet. These apps were available on the Google Play store,” he adds.
On Telegram, a free and popular multiplatform messaging app with enhanced privacy and encryption features, ESET found dozens of groups promoting malicious copies of cryptocurrency mobile wallets. We assume these groups were created by the threat actor behind this scheme looking for further distribution partners and this activity is ongoing since May 2021. Starting in October 2021, we found that these Telegram groups were shared and promoted in at least 56 Facebook groups with the same goal – to search for more distribution partners. In November 2021, we spotted the distribution of malicious wallets, using two legitimate Chinese websites.
Besides these distribution vectors, we discovered dozens of other counterfeit wallet websites that are targeting mobile users exclusively. Visiting one of the websites might lead a potential victim to download a trojanized wallet app for Android or the iOS platform.
The malicious app behaves differently depending on the operating system it was installed on. On Android, it appears to target new cryptocurrency users who do not yet have a legitimate wallet application installed on their devices. On iOS, the victim can have both versions installed – the legitimate one from the App Store and the malicious one from a website.
Regarding iOS, these malicious apps are not available on the App Store; they must be downloaded and installed using configuration profiles, which add an arbitrary trusted code-signing certificate. With regard to Google Play, based on our request as a Google App Defense Alliance partner, in January 2022, Google removed 13 malicious applications found on the official store.
Moreover, it seems that the source code of this threat has been leaked and shared on a few Chinese websites, which might attract various threat actors and spread this threat even further.
“At the time of publication, the price of bitcoin has decreased almost by half from its all-time high about four months ago. For cryptocurrency investors, this might be a time either to panic and withdraw their funds, or for newcomers to jump at this chance and buy cryptocurrency for a lower price. If you belong to one of these groups, you should pick carefully which mobile app to use for managing your funds,” advises Štefanko.
For more technical information, check out the blogpost “Crypto malware in patched wallets targeting Android and iOS devices” on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
Timeline of the scheme
About ESET
ESET develops software solutions that deliver instant, comprehensive protection against evolving computer security threats. ESET pioneered and continues to lead the industry in proactive threat detection. ESET NOD32 Antivirus, its flagship product, consistently achieves the highest accolades in all types of comparative testing and is the foundational product that builds out the ESET product line to include ESET Smart Security. ESET Smart Security is an integrated antivirus, antispyware, antispam and personal firewall solution that combines accuracy, speed and an extremely small system footprint to create the most effective security solution in the industry. Both products have an extremely efficient code base that eliminates the unnecessary large size found in some solutions. This means faster scanning that doesn’t slow down computers or networks. Sold in more than 160 countries, ESET has worldwide production headquarters in Bratislava, SK and worldwide distribution headquarters in San Diego, U.S. ESET also has offices in Bristol, U.K.; Buenos Aires, AR; Prague, CZ; and is globally represented by an extensive partner network. For more information, visit our local office at https://eset.version-2.sg.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The Company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which includes Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities. For more information, please visit https://www.version-2.com.sg/ or call (65) 6296-4268.

