Traveling your Zero Trust journey with ESET
Created: 2023-05-08 08:11:02

Zero Trust seeks to transform how we secure business processes but not to the detriment of people
In one sense, preaching under the banner of “Zero Trust” can feel misleading because if you don’t really trust anyone, you had better close up shop. Can you run a business if you can’t trust your employees, at least to some degree? If that banner were to read “Zero Unverified Trust”, that would explain itself much better, even if it is a less catchy phrase, because it clearly denotes that trust should be verified.
Traditionally, trust was granted rather freely to employees within the perimeter of a business’s network. With the revelation of international hacking attempts and incidents like the Morris worm in the 1980s, IT administrators were strongly reminded about the need to lock down access at their network perimeters. However, cloud infrastructure became increasingly popular in subsequent decades, making fuzzy the concept of a perimeter, and a perimeter-only defense security approach increasingly unfitting.
The concept of Zero Trust originated in 2009 when Forrester pointed out the need for a better approach to handling trust and, thus, for a new security model to replace the traditional perimeter-based approach. Despite the unqualified use of the term “zero”, the goal of the Zero Trust model is not to revoke all trust, but to consider more carefully when to give trust, and then monitor the trust that is given, along with the time and resources given it.
Challenges to implementing Zero Trust
The main contribution of the Zero Trust model is its call to verify and constantly reevaluate the trust given. To achieve this, at least two challenges must be addressed.
First, trust controls may fail to account for employees’ workflows fully or cause frustration if employees or clients feel they deserve more trust. Trust is complex because human behavior is complex, the tools used are varied, and business processes, resources, and staff can change frequently or unexpectedly.
For trust policies not to cause disruption, IT admins need to tailor them to the business’s processes, test them before deployment, and monitor them assiduously. This will require the IT staff to understand the business better.
Second, the business may lack the budget to invest in technologies that help enforce, monitor, and reevaluate the trust assigned. But even if the budget is lacking, there’s a good chance that existing tools and resources can be repurposed à la Zero Trust.
For example, IT admins can increase the collection of logs about user activity and access to company resources, analyze the logs to understand normal patterns and spot anomalies, or fine-tune the permissions and configurations in existing tools. Even if you have already taken these steps, you can do them again with a Zero Trust vision in mind – thinking about how to grant trust only to specific resources and for a specified time, and, as much as possible, how to monitor that trust once given. This should lead to different practical outcomes that can improve the business’s security posture.
Supporting your Zero Trust journey
ESET’s security technologies can support organizations from small businesses to large enterprises on their road to Zero Trust. An easy way to depict the comprehensiveness of the support we provide is with the following pyramid:
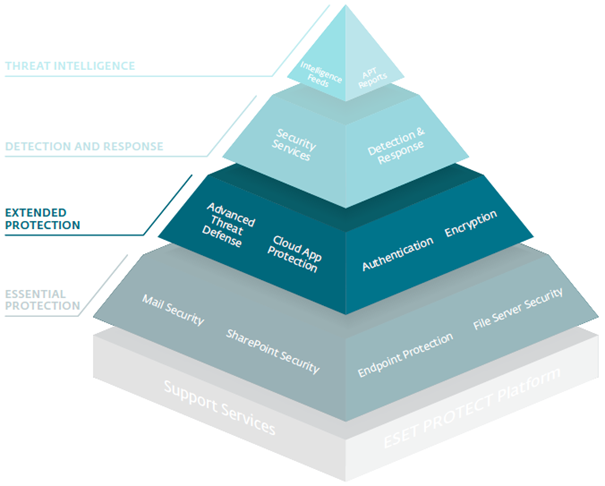
The pyramid sits on a bedrock layer made up of the ESET PROTECT Platform and Support Services. ESET PROTECT consists of various slices from ESET’s suite of protective technologies depicted in the pyramid’s layers above. Support services make ESET’s experts available to your staff to help ensure the best configuration of ESET products for your particular security needs and environment.
Using a pyramid can help to visualize your level of investment into technologies that support Zero Trust. Roughly speaking, the technologies at a higher layer either build on or extend the protection of those at a lower layer. Let’s quickly go through the layers from bottom to top.
The lowest layer contains technologies indispensable for business security, like endpoint protection; therefore, we characterize this as essential protection. At the extended protection layer, we find technologies to help address specific business security needs or fend off advanced threats.
Detection and response, the next layer up, is a game changer because it flips a business’s security posture from reactive to proactive. With ESET’s detection and response tool – ESET Inspect – deployed, security defenders are empowered to monitor and investigate low-level events happening on endpoints in their network.
Finally, the pyramidion at the peak of the pyramid, called threat intelligence, contains threat data feeds and advanced persistent threat (APT) reports. These reports are chock-full of research and technical analysis of new threats, available by subscription only.
In short, the pyramid above lays out some of the technologies that should accompany an organization’s Zero Trust journey. Of course, every company has its own needs fueled by local regulations, the nature of the business, the available IT security budget, and the current state of its IT infrastructure – meaning that your investment in the ESET PROTECT platform serves as no more than a rough guide on what is necessarily a bespoke security journey. What the ESET PROTECT offering does make clear is that it can be a reliable partner at multiple stages of this journey.
About ESET
ESET develops software solutions that deliver instant, comprehensive protection against evolving computer security threats. ESET pioneered and continues to lead the industry in proactive threat detection. ESET NOD32 Antivirus, its flagship product, consistently achieves the highest accolades in all types of comparative testing and is the foundational product that builds out the ESET product line to include ESET Smart Security. ESET Smart Security is an integrated antivirus, antispyware, antispam and personal firewall solution that combines accuracy, speed and an extremely small system footprint to create the most effective security solution in the industry. Both products have an extremely efficient code base that eliminates the unnecessary large size found in some solutions. This means faster scanning that doesn’t slow down computers or networks. Sold in more than 160 countries, ESET has worldwide production headquarters in Bratislava, SK and worldwide distribution headquarters in San Diego, U.S. ESET also has offices in Bristol, U.K.; Buenos Aires, AR; Prague, CZ; and is globally represented by an extensive partner network. For more information, visit our local office at https://eset.version-2.sg.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The Company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which includes Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities. For more information, please visit https://www.version-2.com.sg/ or call (65) 6296-4268.

