ESET Research: North Korea-linked Lazarus impersonates Meta on LinkedIn to attack an aerospace company in Spain
Created: 2023-10-04 08:04:04
- ESET researchers discovered a Lazarus attack against an aerospace company in Spain. Lazarus is a North Korea-linked advanced persistent threat (APT) group.
- Employees of the targeted company were contacted by a fake recruiter via LinkedIn and tricked into opening a malicious executable file presenting itself as a coding challenge or quiz.
- The most notable payload is the LightlessCan backdoor, implementing techniques to hinder detection by real-time security monitoring software and analysis by cybersecurity professionals.
- The final goal of the attack was cyberespionage.
BRATISLAVA, PRAGUE — September 29, 2023 — ESET researchers have uncovered a Lazarus attack against an aerospace company in Spain, in which the group deployed several tools, most notably the newly discovered backdoor named LightlessCan by ESET. Operators of the North Korea-linked Lazarus group obtained initial access to the company’s network last year after a successful spearphishing campaign, masquerading as a recruiter for Meta — the company behind Facebook, Instagram, and WhatsApp. The final goal of the attack was cyberespionage.
“The most worrying aspect of the attack is the new type of payload, LightlessCan, a complex and possibly evolving tool that exhibits a high level of sophistication in its design and operation, and represents a significant advancement in malicious capabilities compared to its predecessor, BlindingCan,” explains ESET researcher Peter Kálnai, who made the discovery.
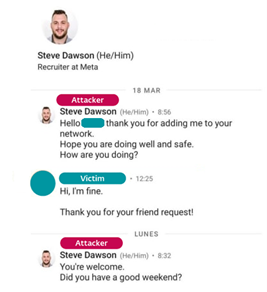
The fake recruiter contacted the victim via LinkedIn Messaging, a feature within the LinkedIn professional social networking platform, and sent two coding challenges supposedly required as part of a hiring process, which the victim downloaded and executed on a company device. ESET Research was able to reconstruct the initial access steps and analyze the tool set used by Lazarus thanks to cooperation with the affected aerospace company. The group targeted multiple company employees.
Lazarus delivered various payloads to the victims’ systems; the most notable is a previously publicly undocumented and sophisticated remote access trojan (RAT) that we named LightlessCan. The trojan mimics the functionalities of a wide range of native Windows commands, usually abused by the attackers enabling discreet execution within the RAT itself instead of noisy console executions. This strategic shift enhances stealth, making detecting and analyzing the attacker’s activities more challenging.
Another mechanism used to minimize exposure is the employment of execution guardrails: Lazarus made sure the payload could be decrypted only on the intended victim’s machine. Execution guardrails are a set of protective protocols and mechanisms implemented to safeguard the integrity and confidentiality of the payload during its deployment and execution, effectively preventing decryption on unintended machines, such as those of security researchers.
LightlessCan has support for up to 68 distinct commands, but in the current version, 1.0, only 43 of those commands are implemented with some functionality. ESET Research has identified four different execution chains, delivering three types of payloads.
The Lazarus group (also known as HIDDEN COBRA) is a cyberespionage group linked to North Korea that has been active since at least 2009. The diversity, number, and eccentricity in implementation of Lazarus campaigns define this group, which performs all three pillars of cybercriminal activities: cyberespionage, cybersabotage, and pursuit of financial gain. Aerospace companies are not an unusual target for North Korea-aligned APT groups. The country has conducted multiple advanced missile tests that violate United Nations Security Council resolutions.
For more technical information about Lazarus, its latest attack, and the LightlessCan backdoor, check out the blog post “Lazarus luring employees with trojanized coding challenges: The case of a Spanish aerospace company” on WeLiveSecurity. ESET Research will present findings about this attack at the Virus Bulletin conference on October 4, 2023. Make sure to follow ESET Research on Twitter (today known as X) for the latest news from ESET Research.
The initial contact by the attacker impersonating a recruiter from Meta
About ESET
ESET develops software solutions that deliver instant, comprehensive protection against evolving computer security threats. ESET pioneered and continues to lead the industry in proactive threat detection. ESET NOD32 Antivirus, its flagship product, consistently achieves the highest accolades in all types of comparative testing and is the foundational product that builds out the ESET product line to include ESET Smart Security. ESET Smart Security is an integrated antivirus, antispyware, antispam and personal firewall solution that combines accuracy, speed and an extremely small system footprint to create the most effective security solution in the industry. Both products have an extremely efficient code base that eliminates the unnecessary large size found in some solutions. This means faster scanning that doesn’t slow down computers or networks. Sold in more than 160 countries, ESET has worldwide production headquarters in Bratislava, SK and worldwide distribution headquarters in San Diego, U.S. ESET also has offices in Bristol, U.K.; Buenos Aires, AR; Prague, CZ; and is globally represented by an extensive partner network. For more information, visit our local office at https://eset.version-2.sg.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The Company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which includes Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities. For more information, please visit https://www.version-2.com.sg/ or call (65) 6296-4268.

