ESET Research discovers Operation Jacana, targeting governmental entity in Guyana, likely by Chinese threat group
Created: 2023-10-09 06:01:55
- ESET Research discovered Operation Jacana, a targeted cyberespionage campaign against a Guyanese governmental entity.
- After the initial compromise via spearphishing emails, the attackers proceeded to move through the victim's internal network.
- To extract sensitive data, the operators used a previously undocumented backdoor we named DinodasRAT.
- Apart from DinodasRAT, the attackers also deployed Korplug, leading ESET to suspect that China-aligned operators are behind this operation.
- Based on the emails used to gain initial access to the victim’s network, the operators are keeping track of the political activities of their victims.
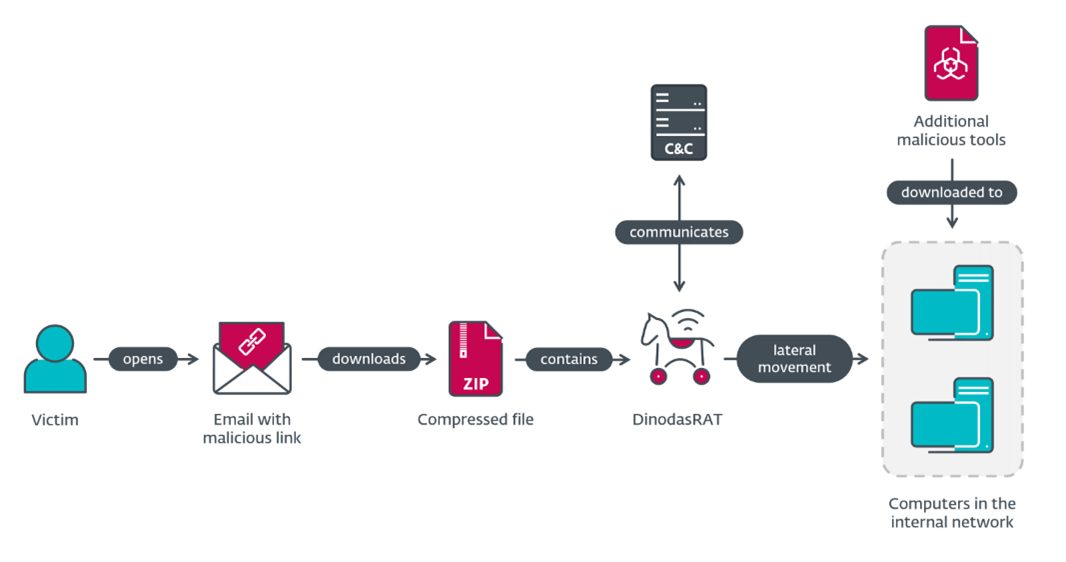
BRATISLAVA, MONTREAL — October 5, 2023 — ESET researchers discovered a cyberespionage campaign against a governmental entity in Guyana. Named Operation Jacana by ESET, we believe with medium confidence that it is linked to a China-aligned threat group. In the attack, the operators used a previously undocumented backdoor, DinodasRAT (Remote Access Trojan), that can exfiltrate files, manipulate Windows registry keys, and execute commands, and it encrypts the information it sends to the command and control server (C&C) using the Tiny Encryption Algorithm.
This campaign was targeted, as the threat actors crafted their emails specifically to entice their chosen victim organization. After successfully compromising an initial but limited set of machines with DinodasRAT, the operators proceeded to move inside and breach the target’s internal network, where they again deployed this backdoor. It has various capabilities that allow an attacker to spy on and collect sensitive information from a victim’s computer. Other malicious tools, such as a variant of Korplug (aka PlugX), were also deployed.
Korplug is common to China-aligned groups, for example, Mustang Panda. The attribution to a China-aligned threat actor is made with only medium confidence. This attribution is further supported by recent developments in Guyana–China diplomatic relations. In February 2023, the same month that Operation Jacana took place, the Special Organized Crime Unit of Guyana arrested three people in a money-laundering investigation involving Chinese companies, an act disputed by the local Chinese embassy.
The deployed spearphishing emails referenced recent Guyanese public and political affairs, indicating that the attackers are keeping track of their victims’ (geo)political activities to increase the likelihood of the operation’s success. One email, luring the victims with news concerning a “Guyanese fugitive in Vietnam,” contained a domain ending with gov.vn. “This domain indicates a Vietnamese governmental website; thus, we believe that the operators were able to compromise a Vietnamese governmental entity and use its infrastructure to host malware samples. ESET researchers notified the VNCERT about the compromised infrastructure,” says ESET researcher Fernando Tavella, who discovered Operation Jacana.
ESET researchers have named the backdoor DinodasRAT based on the victim identifier it sends to its C&C server: the string always begins with Din, which reminded us of the hobbit Dinodas from the Lord of the Rings by J.R.R. Tolkien. On the other hand, wattled jacanas are birds native to Guyana; they sport large claws on their feet, allowing them to walk on floating plants in the lakes they inhabit.
For more technical information about Operation Jacana and the DinodasRAT backdoor, check out the blog post “Operation Jacana: Foundling hobbits in Guyana” on WeLiveSecurity. Make sure to follow ESET Research on Twitter (today known as X) for the latest news from ESET Research.
Operation Jacana compromise flow
About ESET
ESET develops software solutions that deliver instant, comprehensive protection against evolving computer security threats. ESET pioneered and continues to lead the industry in proactive threat detection. ESET NOD32 Antivirus, its flagship product, consistently achieves the highest accolades in all types of comparative testing and is the foundational product that builds out the ESET product line to include ESET Smart Security. ESET Smart Security is an integrated antivirus, antispyware, antispam and personal firewall solution that combines accuracy, speed and an extremely small system footprint to create the most effective security solution in the industry. Both products have an extremely efficient code base that eliminates the unnecessary large size found in some solutions. This means faster scanning that doesn’t slow down computers or networks. Sold in more than 160 countries, ESET has worldwide production headquarters in Bratislava, SK and worldwide distribution headquarters in San Diego, U.S. ESET also has offices in Bristol, U.K.; Buenos Aires, AR; Prague, CZ; and is globally represented by an extensive partner network. For more information, visit our local office at https://eset.version-2.sg.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The Company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which includes Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities. For more information, please visit https://www.version-2.com.sg/ or call (65) 6296-4268.

