Multiple factors complicate admin decisions involving threat mitigation and remediation. Alert fatigue, from sifting through myriad detections and dashboard clutter all have costs: human, time, security, and financial. In response, ESET has engineered more clarity into our detection and response module, paying big dividends for budget holders and security admins alike.
New functions in ESET Inspect, the XDR-enabling component within our unified cybersecurity platform ESET PROTECT, assist security admins in correlating detections to related entities.
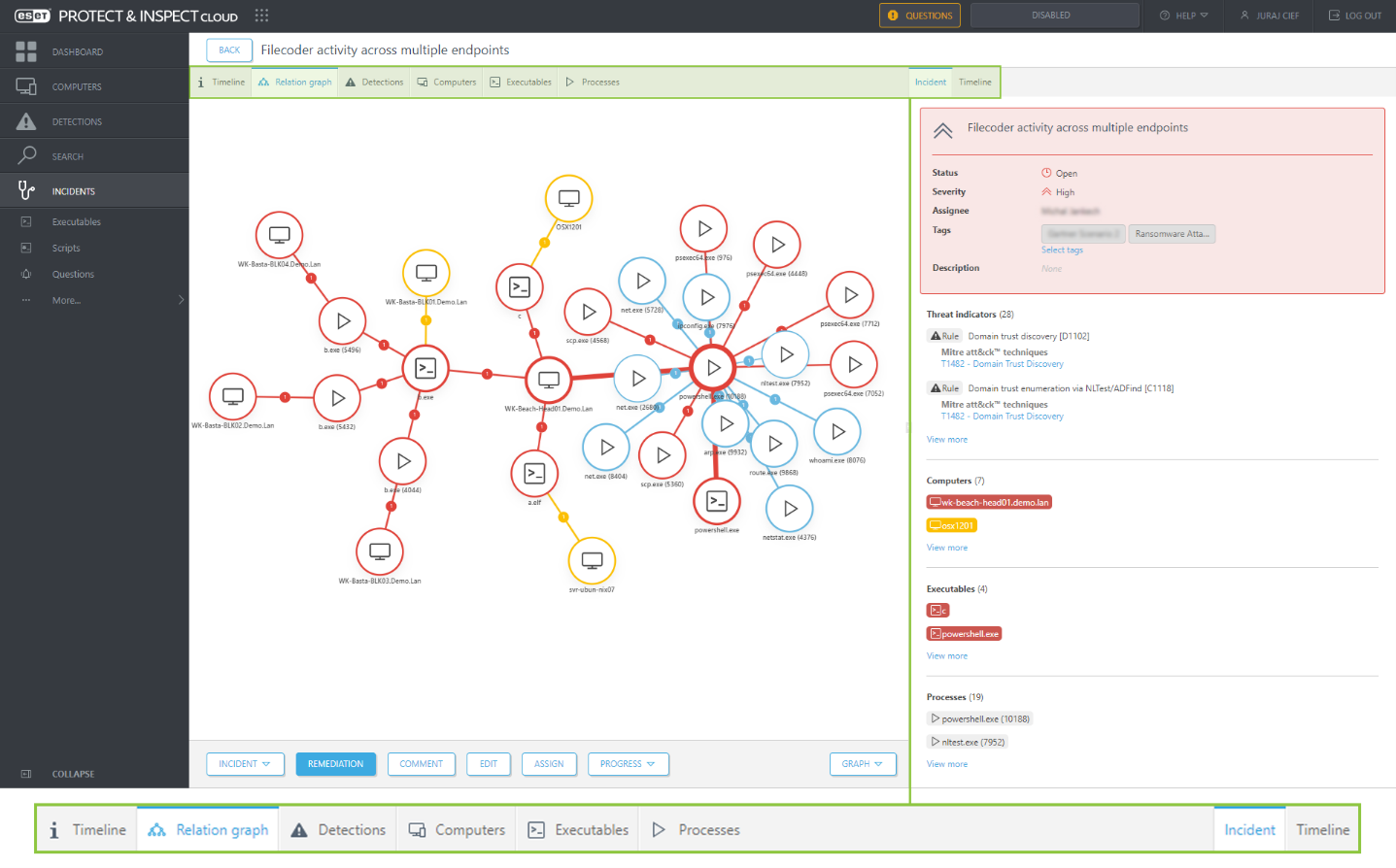
Image 1: Incident Creator displays multiple prioritized entities to reduce alerts and simplify admin decision points concerning mitigation and remediation options including: Timeline, Relation Graph, Detections, Computers, Executables, Processes, Incident.
Investigating incidents through the lens of these related entities supersedes the need to filter through large numbers of detections. And, only, when necessary, would the admin need to drill down deeper to the level of detections -related to the incidents- as well as the events that triggered those detections.
Improved efficiencies around these tasks have been delivered in ESET Inspect via the new Incident Creator feature, which performs a correlation of detections and entities. This correlation enables IT security admins to visualize the relationships between multiple prioritized network entities by recognizing patterns across detections and entities, and intelligently grouping these critical clues into incidents.
Quick takeaway – ESET Inspect Incident Creator
The representation (image below) shows the correlation of entities (interactions between tools, files, and even systems) generated by the Incident Creator. In it, an admin can quickly determine the relationship between the detection of Filecoder malware, aka Ransomware, and other incidents detected by ESET PROTECT (our unified cybersecurity platform).
In this case, the admin viewing the dashboard can immediately gain an overview of what’s happening or what has already happened. They are provided with prioritized context concerning severity and other crucial information via a system of tags and alerts. Depending on the admin’s maturity, they might (for example) skip the MITRE ATT&CK linked tactics techniques and procedures, with their eyes drawn instead to the number of machines affected or detected executables.
At the center, we see a specific machine (wk-beach-head01.dem.lan) surrounded by a red circle denoting the severity (Red = Threat, Yellow= Warning, Blue= Info) of the detection. The admin can quickly identify a number of executables and related prioritized processes at work. Two executables stand out here: (c.) and (powershell.exe). These are highlighted in red in the image below.
The clear layout of the incident “Pane” (at right) allows a quick appraisal of the situation. With their eyes moving back to the Incident Creator graph, a pattern of lateral movement quickly emerges. The admin can see incidents that not only affect Windows machines, but also Linux (Ubuntu Server) and macOS machines with dedicated scripts.
The dashboard also clearly highlights both the abused legitimate tools (in blue) as well as dedicated malware scripts and executables* in (red). This literally helps connect the dots, a big plus with quick remediation and incident response phases but is also helpful with later forensic analysis.
*Another machine, osx1201, circled in Yellow (warning), is also located in relation to a critical executable.
The never-ending search for experience
Since neither detection and response tools nor the staff that operate them come cheap, companies logically demand concrete return on investment once detection and response is deployed. The Incident Creator capability thus supplies a notable boost to the analytic logic needed by admins, threat hunters, and SOC teams to raise security via improved configuration options, for example. These can be applied either to increase the detection sensitivity if they are more risk-averse, or to create exceptions suited to their specific environments to reduce noise. This ultimately requires staff to employ their knowledge and confirm the organization’s trust in solid events analysis and correctly prioritizing protection decisions.
An admin consulting a dashboard where the correlation between these factors is visualized becomes a faster learner, more confident, and a more competent defender. A defender that can look beyond the automated categories of monitoring and detection found in an endpoint protection product and track cyber threats where some imprint of misused human intelligence may lay.
Hiring vs. building a top-flight admin . . . at the right cost
Laying hands-on mature IT security staff/Security Operations Center (SOC) staff has become the number one job for many CISOs and their HR recruiters. Once candidates are located, there is the inevitable moment when the elephant in the room comes into view, and the question is asked if the candidate has enough practical experience with detection and response products and processes to make an impact.
The reasons for caution are widespread, but as much as detection and response tools are proven to provide a powerful set of insights into a network and its endpoints, their use is demanding. Experienced admins are even harder to secure than cost-effective products.
Identifying a product that pairs great visibility and usability, with proportionately low total cost of ownership (TCO) ratings and features supporting on-the-job maturation, becomes a critical part of the equation. Many of these critical attributes are explored at a high level by tests like AV-Comparatives recent Endpoint Prevention & Response (EPR) Test 2023. However, the features supplied by tools like ESET Inspect are what make or break the user experience for Security admins tasked with delivering and improving security on your network.
Closing the gap between the EDR skills and experience possessed by a top-flight admin, versus supporting and maturing a journeyman admin in evolving into a top-flight pro may be best addressed by providing them with the insight necessary to classify threats and prioritize mitigation. Best enabling your team in this regard means providing tools that reduce the burden of analysis and interpretation of data from the detection and response dashboard concerning network incidents and enabling less-experienced IT security admins to understand the relationships between multiple entities.
Human value-add
With more complex threats and attacks, only another human intelligence – that of a security defender – may be able to spot an attack before too much damage is done.
At the minimum, a defender armed with an XDR-enabling module like ESET Inspect with Incident Creator (graphing) is empowered to rapidly contextualize the severity of incidents within their increasing familiarity of the environment. That, and being provided with the right filtering of entities to reconstruct the sequence of steps that an attack followed from start to finish both raises their game and builds further experience and network context while supporting an ever-improving security trend.
Simply put, if the move to detection and response begins with an optimized dashboard that includes incident creation, then the resultant experience gains of your IT admins and steady progress made by your business toward better security will likely be worth the effort.

