The ATT&CK® Evaluations Enterprise 2024 highlights ESET’s AI‑native approach to detection and response
Created: 2024-12-16 08:22:56

NOTE: The views and opinions expressed in this blogpost are those of ESET and do not necessarily reflect the views or positions of MITRE Engenuity.
In this year’s Enterprise edition of the ATT&CK® Evaluations, MITRE set up three attack scenarios: a Democratic People’s Republic of Korea (DPRK) scenario to test cyberespionage activity against a macOS system, a Cl0p scenario to test a ransomware attack against a Windows system, and a LockBit scenario to test a ransomware attack against a corporate environment containing both a Linux server and Windows workstations and servers.
ESET Inspect demonstrated good visibility in each scenario, detecting every step while keeping the total number of detections (or volume) low. The detections generated from the attacks were automatically correlated into incidents by ESET Inspect’s Incident Creator, giving our security analysts a focused view of the attacks and thus a clear understanding of how they happened step-by-step.
To get a better idea of how ESET fared, we will go over some of the methodological changes introduced by MITRE and then look at how Incident Creator streamlined the view and workflow of the security analysts sitting at the ESET Inspect dashboard.
Methodology
This evaluation brought several well-thought-out changes to the methodology of the Detection scenarios that we believe better reflect the security analyst’s work of dealing with real-world cyberattacks.
First, Telemetry is no longer a detection category, meaning that it is not sufficient merely to show that an event occurred. The lowest detection category is now General, requiring a detection to indicate that an event occurred and is suspicious or malicious in some way. It’s important to point out that an event occurring in a sandbox does not qualify as an event occurring in the environment under evaluation. As indicated in its description, a General detection must answer the what, where, when, and who as related to the tested environment, and these cannot be answered from external sandbox execution.
Second, some benign substeps have been baked in as a test for false positives rather than for detections. This is a welcome change because it discourages a “detect everything” approach, which can otherwise create a lot of noise and needless work for the security analyst, and drive up data storage costs to boot. Another benefit of this change is that it allows calculating a precision score, indicating how many of the detections made correspond to actually malicious or suspicious substeps.
Third, some substeps are included but not evaluated. The reason for including such substeps is to better simulate a real-world cyberattack by avoiding illogical jumps in the progression of the attack.
Finally, a volume metric was introduced that records the number of detections shown in the dashboard. This is yet another way of discouraging a “detect everything” approach, dissuading vendors from allowing their dashboards to be populated sometimes with millions of detections. We welcome this adjustment too.
The volume metric also records the severity of detections, using five levels: critical, high, medium, low, and info. Since ESET Inspect has three incident severity levels of high, medium, and low, and three detection severity levels of threat, warning, and info, we agreed with the MITRE Engenuity team on the mapping shown in Table 1.
Table 1. Mapping between ATT&CK Evaluation and ESET Inspect severity levels
|
ATT&CK Evaluation |
ESET Inspect |
|
Critical |
High-severity incident |
|
High |
Threat-severity detection correlated to any incident |
|
Medium |
Warning-severity detection correlated to any incident |
|
Low |
Info-severity detection with score > 22, correlated to any incident |
|
Info |
Info-severity detection with score <=22, correlated to any incident |
It is worth pointing out why we chose a severity score of 22 to divide the low and info severity levels. As noted in our documentation:
Rules with severity 22 and below are telemetry rules. They are usually used only as additional information for investigating an incident and can often be triggered by legitimate behavior. If some of these rules generate too much traffic in your environment, you may consider turning them off.
From here on out, we will refer to severity levels only as used by ESET Inspect.
An important consequence of using this mapping is that detections not correlated to an incident are out of scope in the evaluation. This largely reflects the intended usage of ESET Inspect in the real world: incidents populated by correlated detections are the primary focus for security analysts. Additional detailed information and detections not correlated to incidents, which could be of value in some cases, are secondary.
Since dashboards inevitably have various parts that show detections and other information in detailed, summary, or graphical forms, vendors were allowed to indicate for the evaluation the standard view that security operators are expected to use for handling attacks. Only information presented via this view is eligible for consideration as a detection or false positive, and for measuring volume. In ESET Inspect, the standard view for security analysts is Incidents.
Incidents
The Incidents view is the primary place that security operators should use to manage their workflow. Incidents are automatically populated into this view in two ways:
- ESET Incident Creator, which uses an AI-based engine to correlate detections into a single incident.
- ESET Inspect, which currently has over 100 rules that create an incident as a response to being triggered, aggregating detections into a single incident by affected computers, a period of time, or both.
Operators are recommended to use the following workflow:
- Investigate each incident.
- Investigate threat-severity detections not correlated to any incident, if time allows.
Just as last year’s evaluation, each attack scenario was run twice. Vendors were allowed to make config changes for the second run to try to increase visibility, decrease false positives, and reduce volume. Figure 1 shows the Incidents view after the config change run.
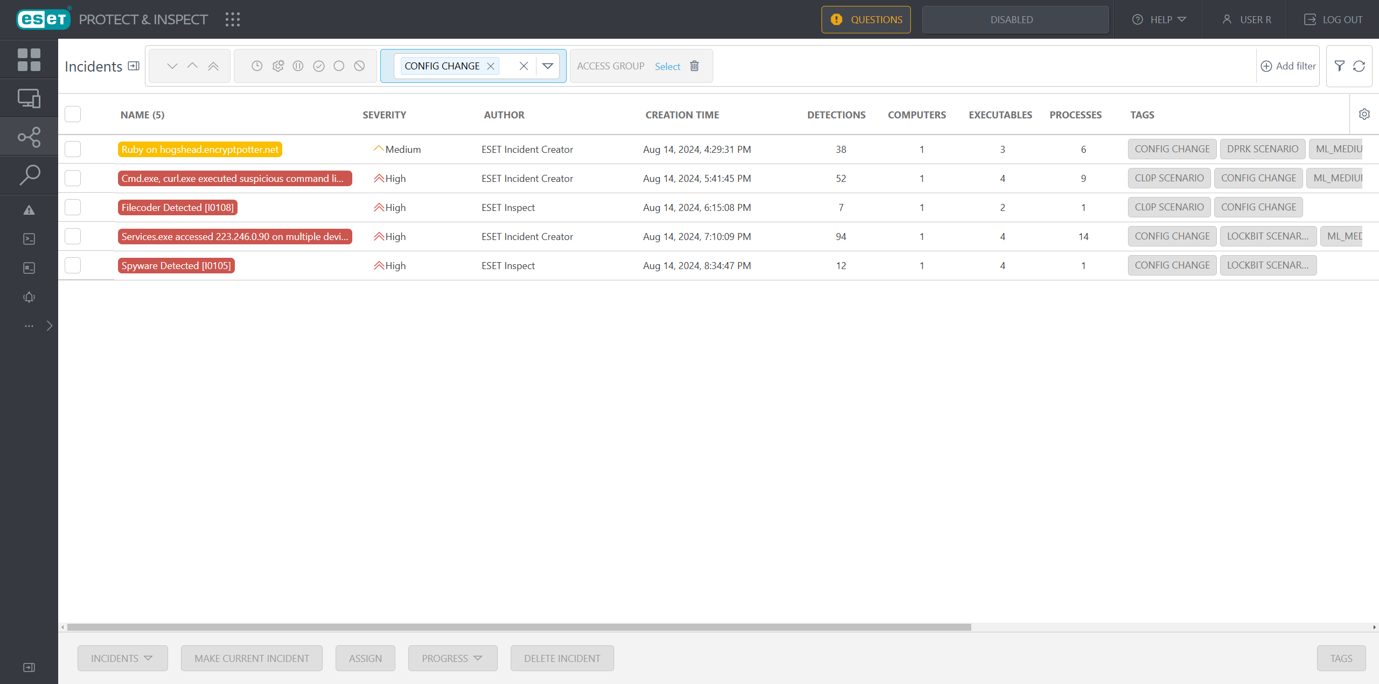
Incident Creator did not generate any false positive incidents during the evaluation. On the contrary, only one or two incidents were created per scenario in the config change run and nearly all relevant detections available in ESET Inspect were correlated to an incident.
Scenario highlights
In the following sections, we will go over highlights from ESET’s results in each scenario.
DPRK
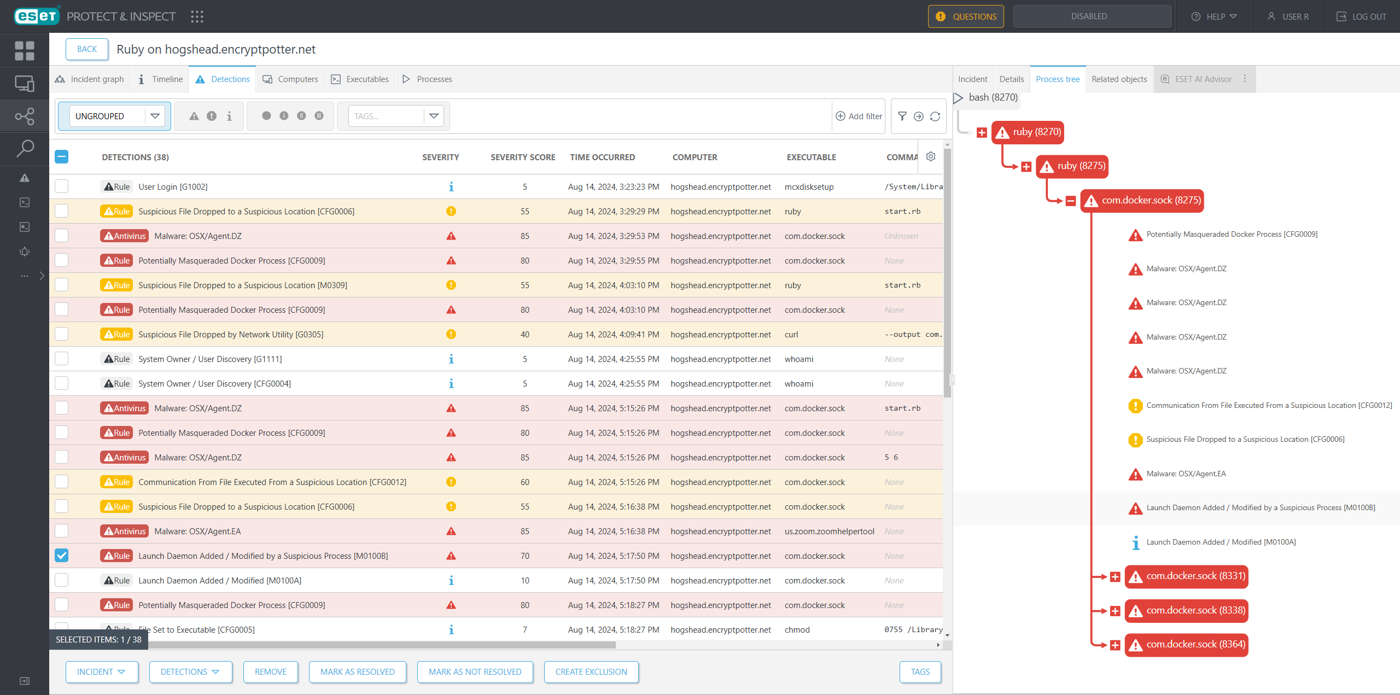
ESET Inspect automatically handled the DRPK scenario as a medium-severity incident created by Incident Creator. Highlights from ESET’s results in this scenario include detection of the two backdoors being dropped to suspicious locations, the backdoor processes masquerading as Docker and Zoom, the theft from keychain files, and no false positives.
Figure 2 shows a part of the incident for the detections correlated to this attack, highlighting a detection for the FULLHOUSE.DOORED backdoor installing persistence for a second-stage backdoor, STRATOFEAR, as a launch daemon.
Cl0p
In the config change run, ESET Inspect automatically handled the Cl0p scenario as two high-severity incidents, one created by Incident Creator and another by a rule that monitors for endpoint detections of filecoders.
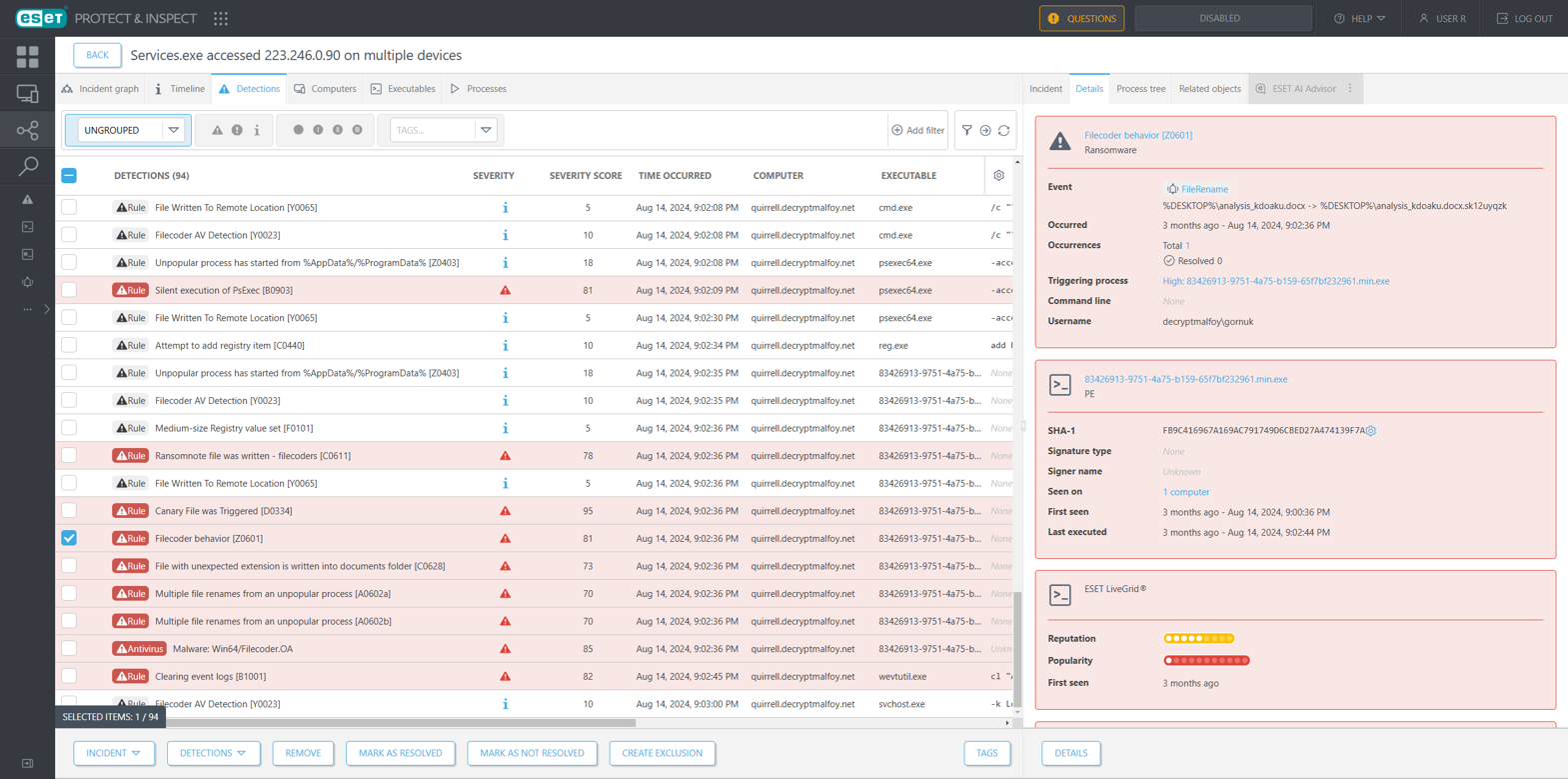
Highlights from ESET’s results in this scenario include detection of loading of the SDBbot installer and loader DLLs, modification of a registry key to achieve persistence for the SDBbot RAT, deletion of shadow copies, disabling of Windows recovery after boot failure, and Cl0p ransomware execution.
Figure 3 shows a part of the incident for the detections correlated to this attack, highlighting a detection for file writes or file renames of canary files for early detection of ransomware execution. The triggered rule not only kills the offending process but also creates an incident in the Incidents view.

LockBit
In the config change run, ESET Inspect automatically handled the LockBit scenario as two high-severity incidents, one created by Incident Creator and another by a rule that monitors for endpoint detections of spyware.
Highlights from ESET’s results in this scenario include detection of the attacker logging in via VNC, modification of a registry value to enable automatic login, using SSH to connect to a Linux server in the internal network, spreading LockBit ransomware to other machines in the network via PsExec, the execution of LockBit, and clearing of Windows event logs to hide intrusion activity.
Figure 4 shows a part of the incident for the detections correlated to this attack, highlighting a detection for a suspicious process writing or renaming files with specific, so-called double extensions – typical filecoder behavior.
Final words
We believe that the summary above paints the best picture of our approach in designing ESET Inspect. It indicates that security analysts can be highly confident that they are efficiently handling real threats whenever ESET Inspect brings an incident with correlated detections to their attention.
Once again, we would like to highlight that the MITRE team has professionally executed another evaluation round, bringing a number of changes to goad vendors into better preparing for the diversity of tactics and techniques played out in the real world rather than for being a “winner” of a competition that does not exist.
On our part, although we are certainly looking to improve ESET Inspect in a few areas to detect additional true positive substeps, this has to be balanced against the risk that dramatically increasing coverage could lower precision and increase volume, all of which would hobble our approach, bringing less and less value for more and more cost.
In short, we hope that ESET’s perspectives on this year’s evaluation has sparked your curiosity to explore our results further on the evaluation page provided by MITRE ATT&CK Evaluations.
About ESET
ESET develops software solutions that deliver instant, comprehensive protection against evolving computer security threats. ESET pioneered and continues to lead the industry in proactive threat detection. ESET NOD32 Antivirus, its flagship product, consistently achieves the highest accolades in all types of comparative testing and is the foundational product that builds out the ESET product line to include ESET Smart Security. ESET Smart Security is an integrated antivirus, antispyware, antispam and personal firewall solution that combines accuracy, speed and an extremely small system footprint to create the most effective security solution in the industry. Both products have an extremely efficient code base that eliminates the unnecessary large size found in some solutions. This means faster scanning that doesn’t slow down computers or networks. Sold in more than 160 countries, ESET has worldwide production headquarters in Bratislava, SK and worldwide distribution headquarters in San Diego, U.S. ESET also has offices in Bristol, U.K.; Buenos Aires, AR; Prague, CZ; and is globally represented by an extensive partner network. For more information, visit our local office at https://eset.version-2.sg.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The Company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which includes Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities. For more information, please visit https://www.version-2.com.sg/ or call (65) 6296-4268.

