Lumma Stealer: A fast-growing infostealer threat
Created: 2025-02-01 12:01:26

In their biannual ESET Threat Report, ESET researchers have revealed a massive rise in detections of Lumma Stealer, which quietly threatens consumers and businesses alike.
ESET Research is back with a frightening statistic — Detections of Lumma Stealer, an infostealer we previously reported as a threat to gamers, increased 369% between H1 and H2 2024. This is problematic, as infostealers like Lumma continue to plague both consumer and business systems, usually without the knowledge of their owners.
While infostealers are a sneaky lot, they are not without their vulnerabilities — which ESET products can capitalize on, to your security benefit.
Let Lumma tell you a story
Also known as LummaC2 Stealer, this malware-as-a-service mostly targets cryptocurrency wallets, user credentials and two-factor authentication browser extensions, but it also tries to exfiltrate various other data from compromised machines.
What is malware-as-a-service (MaaS)?
Not unlike modern software offers, malware-as-a-service is a business model that provides interested parties with ready-made and instantly deployable malware solutions. Typically offered on underground hacking forums found on the dark web, MaaS operators supply a variety of malware either as a one-time purchase or via a subscription. Ultimately, this easy access enables even those without advanced technical skills to launch cyberattacks, increasing their prevalence.
Lumma Stealer first appeared in August 2022 and is available for sale through a tiered pricing structure on hacking forums and Telegram. The cost ranges from $250 to $20,000, with the most expensive tier letting buyers access the infostealer’s source code — enabling-would-be criminals to act as resellers.
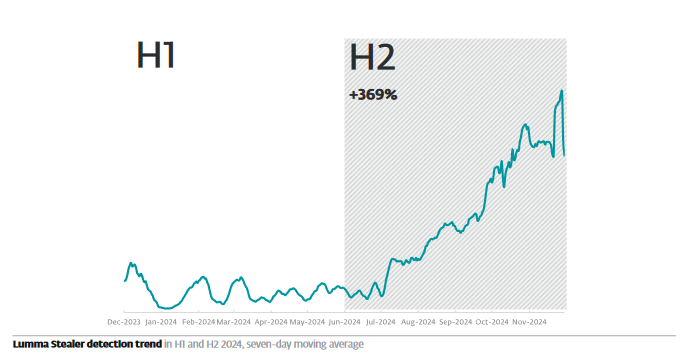
Because Lumma is a ready-made malware solution, it is easier for novice threat actors to share around. Its ease of use and breadth of functions alone make it an attractive choice for would-be attackers — but the fact that it can be spread through multiple vectors, unnoticed, makes it even more useful.
Exploring attack vectors and ESET telemetry
While Lumma Stealer can spread through a variety of distribution vectors, some methods are more clever than others. One particularly sophisticated campaign discovered in October 2024 delivered Lumma Stealer through fake CAPTCHA sites, which, after successful “verification,” delivered the infostealer onto the victim’s device.
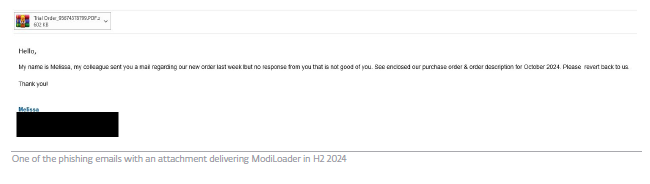
Other avenues enabling Lumma Stealer’s spread include cracked installations of popular open-source or paid apps such as ChatGPT or Vegas Pro. The infostealer can also spread via phishing emails or Discord messages, making it more likely to land in the inbox of even the youngest online users.
Did you know?
Message boards like Discord can play a major role in the spread of malicious software and scams. This is due to the way such places act as a kind of digital crossroads for online human activity, making them ripe for abuse. Moreover, threat actors can abuse the content delivery networks of such online/cloud platforms to distribute malware, as well.
ESET also detected a campaign in which the Win/Rozena.ADZ injector delivered Lumma Stealer via compromised videos on online marketplaces and websites with adult content. Likewise, Lumma Stealer was detected in KMS activators for pirated copies of Windows.
Last but not least, in June 2024, ESET Research reported that players of the popular Hamster Kombat mobile clicker game were being targeted, with cryptors containing Lumma Stealer hidden on GitHub repositories in the guise of helpful automation tools for the game.
Just one of many infostealers on the loose
ESET telemetry for H2 2024 registered the highest number of Lumma Stealer attack attempts in Peru, Poland, Spain, Mexico and Slovakia. However, Lumma is not the only infostealer going around, and in general, the top five countries targeted by infostealer attacks in H2 2024 were Japan, Spain, Turkey, Poland and Italy.
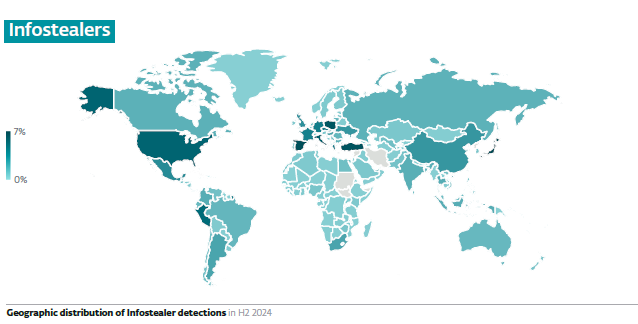
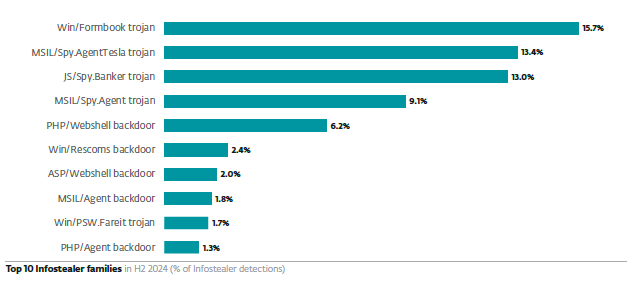
Among other notable infostealers is Formbook, first discovered in 2016 and mainly spread through email phishing. This infostealer collects clipboard data, keystrokes, screenshots and cached browser data, and uses sophisticated obfuscation techniques to prevent deeper analysis. Moreover, it’s been detected as part of large-scale ModiLoader and AceCryptor campaigns in Central and Eastern European states such as Poland, Romania, Czechia and Croatia.
Spy another day
Infostealers are so damaging because being compromised even for a short time can be quite disastrous for both individuals and businesses. Once an infostealer gathers sufficient data to steal someone’s credentials, funds, or identity, that individual can lose funds (crypto or cash), access to personal accounts, and more. Compromised businesses can experience such costly cyber incidents as network infiltration, data breaches, extortion and ransomware attacks.
Fortunately, there are many ways to prevent infostealers and similar threats from infiltrating our devices:
- Get endpoint security: The easiest way to prevent most malware from making a mess of our systems is to install an endpoint security solution with real-time protection. ESET Endpoint Security or ESET Home Security offer such a solution, thanks to multilayered ESET LiveSense technology that protects without hindering computer performance.
- Block: Another good practice is to block popups and ads in browsers, as they can sometimes lead to malware downloads. In addition, consider increasing your browser security and privacy settings, as these restrict how much data can flow between a website/cookies and your in-browser activities/PC. Alternatively, use a secure browser (such as the one contained in ESET security products) for safer banking and browsing.
- Update: Keep every device updated. Known vulnerabilities are still highly exploited, as people tend to leave their systems unpatched, leading to data breaches and data exfiltration.
- Verify: Never click on random links or open any attachments that look suspicious, as these can harbor malware. Likewise, try not to download cracked or seemingly “free” software, and opt to use legitimate marketplaces to prevent accidental infostealer attacks.
Lumma looms on the horizon
Threats such as Lumma Stealer don’t distinguish whether the user being victimized is a child, an adult, or a business; they just spread by diverse means and take whatever they can to further malicious agendas. While increasing your awareness of infostealers and how they work is a great first step toward decreasing the chance of a human error-induced compromise, the rising sophistication and presence of infostealers online make it wise to patch up any newly discovered security gaps before they invite bad actors.
So don’t pass up on device security, and be mindful of risks in the digital world, as you can never know what you might encounter.
About ESET
ESET develops software solutions that deliver instant, comprehensive protection against evolving computer security threats. ESET pioneered and continues to lead the industry in proactive threat detection. ESET NOD32 Antivirus, its flagship product, consistently achieves the highest accolades in all types of comparative testing and is the foundational product that builds out the ESET product line to include ESET Smart Security. ESET Smart Security is an integrated antivirus, antispyware, antispam and personal firewall solution that combines accuracy, speed and an extremely small system footprint to create the most effective security solution in the industry. Both products have an extremely efficient code base that eliminates the unnecessary large size found in some solutions. This means faster scanning that doesn’t slow down computers or networks. Sold in more than 160 countries, ESET has worldwide production headquarters in Bratislava, SK and worldwide distribution headquarters in San Diego, U.S. ESET also has offices in Bristol, U.K.; Buenos Aires, AR; Prague, CZ; and is globally represented by an extensive partner network. For more information, visit our local office at https://eset.version-2.sg.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The Company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which includes Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities. For more information, please visit https://www.version-2.com.sg/ or call (65) 6296-4268.

