ESET Research investigates RansomHub, dives into EDR killers, uncovers ties among rival gangs
Created: 2025-03-31 07:30:10
- ESET Research releases its analysis of the current ransomware ecosystem with focus on ransomware-as-a-service gang RansomHub.
- ESET discovered links between the RansomHub, Play, Medusa, and BianLian ransomware gangs by following the trail of tooling that RansomHub offers its affiliates.
- ESET analysis documents findings about EDRKillShifter and offers insights into the emerging threat of EDR killers.
PRAGUE, BRATISLAVA — March 26, 2025 — ESET researchers have released a deep-dive analysis about significant changes in the ransomware ecosystem, with focus on the newly emerged and currently dominating ransomware-as-a-service gang RansomHub. The report shares previously unpublished insights into RansomHub’s affiliate structure and uncovers clear connections between this newly emerged giant and well-established gangs Play, Medusa, and BianLian. Furthermore, ESET highlights the emerging threat of Endpoint Detection and Response (EDR) killers, unmasking EDRKillShifter, a custom EDR killer developed and maintained by RansomHub. ESET has observed an increase in ransomware affiliates using EDR killer code derived from publicly available proofs of concept, while the set of drivers being abused is largely unchanged.
“The fight against ransomware reached two milestones in 2024: LockBit and BlackCat, formerly the top two gangs, dropped out of the picture. And for the first time since 2022, recorded ransomware payments dropped significantly by a stunning 35%. On the other hand, the recorded number of victims announced (to be outed publicly) on dedicated leak sites increased by roughly 15%. A big part of this increase is due to RansomHub, a new ransomware-as-a-service (RaaS) gang that emerged around the time of law-enforcement Operation Cronos, which disrupted LockBit activities,” says ESET researcher Jakub Souček, who investigated RansomHub.
Just as any emerging RaaS gang, RansomHub needed to attract affiliates — who rent ransomware services from operators — and since there is strength in numbers, the operators weren’t very picky. The initial advertisement was posted on the Russian-speaking RAMP forum in early February 2024, eight days before the first victims were posted. RansomHub prohibits attacking nations from the post-Soviet Commonwealth of Independent States, Cuba, North Korea, or China. Interestingly, it lures affiliates in with the promise that they will receive the whole ransom payment to their wallet, and the operators trust the affiliates to share 10% with them, something quite unique.
In May, RansomHub operators made a significant update: They introduced their own EDR killer — a special type of malware designed to terminate, blind, or crash the security product installed on a victim’s system — typically by abusing a vulnerable driver.
RansomHub’s EDR killer, named EDRKillShifter, is a custom tool developed and maintained by the gang. EDRKillShifter is offered to RansomHub affiliates. Functionality-wise, it is a typical EDR killer targeting a large variety of security solutions that the RansomHub operators expect to find protecting the networks they aim to breach.
“The decision to implement a killer and offer it to affiliates as part of the RaaS program is rare. Affiliates are typically on their own to find ways to evade security products — some reuse existing tools, while more technically oriented ones modify existing proofs of concept or utilize EDR killers available as a service on the dark web. ESET researchers saw a steep increase in the use of EDRKillShifter, and not exclusively in RansomHub cases,” explains Souček.
Advanced EDR killers consist of two parts — a user mode component responsible for orchestration (the killer code) and a legitimate, but vulnerable, driver. The execution is typically very straightforward — the killer code installs the vulnerable driver, typically embedded in its data or resources, iterates over a list of process names of security software, and issues a command to the vulnerable driver, resulting in triggering the vulnerability and killing the process from kernel mode. “Defending against EDR killers is challenging. Threat actors need admin privileges to deploy an EDR killer, so ideally, their presence should be detected and mitigated before they reach that point,” adds Souček.
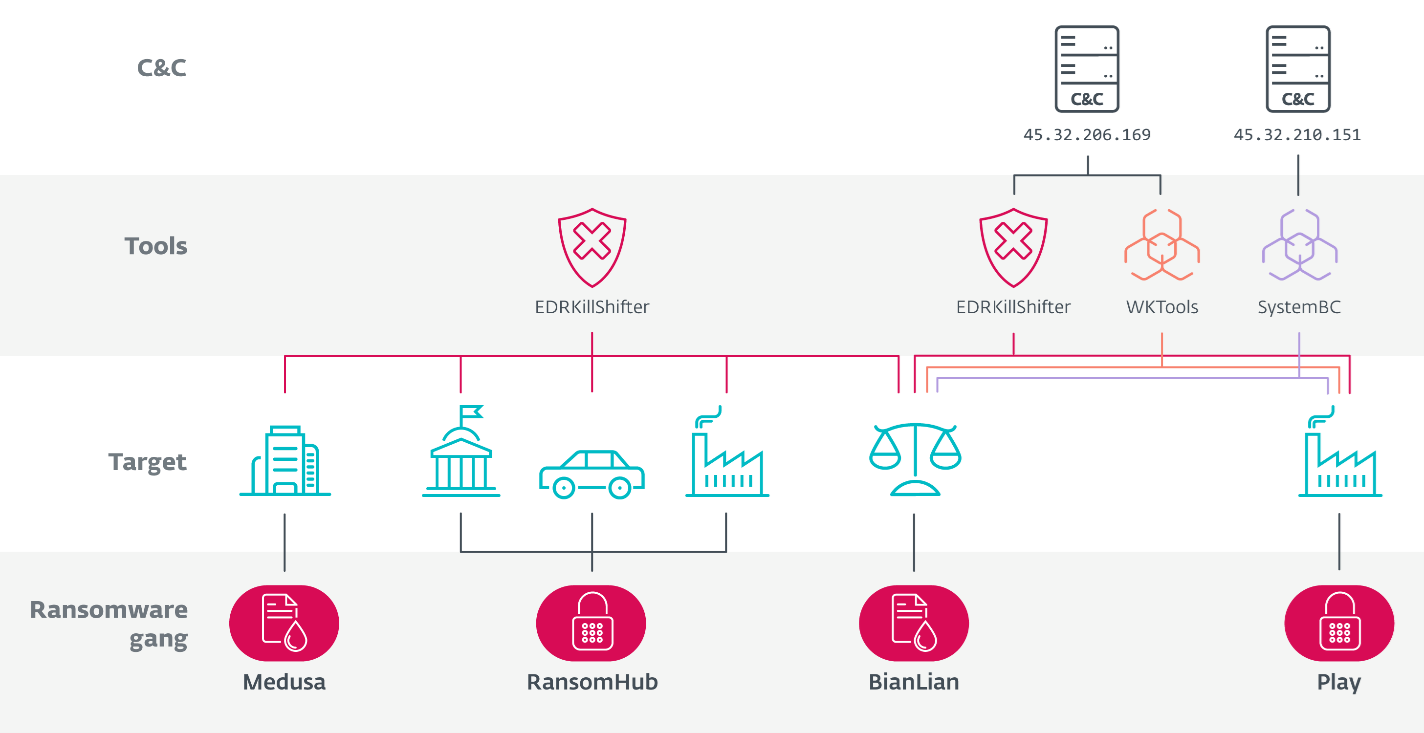
ESET discovered that RansomHub’s affiliates are working for three rival gangs — Play, Medusa, and BianLian. Discovering a link between RansomHub and Medusa is not that surprising, as it is common knowledge that ransomware affiliates often work for multiple operators simultaneously. On the other hand, one way to explain Play and BianLian having access to EDRKillShifter is that they hired the same RansomHub affiliate, which is unlikely given the closed nature of both gangs. Another, more plausible explanation is that trusted members of Play and BianLian are collaborating with rivals, even newly emerged ones like RansomHub, and then repurposing the tooling they receive from those rivals in their own attacks. Play has been linked to the North Korea-aligned group Andariel.
For a more detailed analysis of RansomHub and EDRKillShifter, check out the latest ESET Research blogpost “Shifting the sands of RansomHub’s EDRKillShifter” on WeLiveSecurity.com. Make sure to follow ESET Research on Twitter (today known as X), BlueSky, and Mastodon for the latest news from ESET Research.
Schematic overview of the links between Medusa, RansomHub, BianLian, and Play

About ESET
ESET develops software solutions that deliver instant, comprehensive protection against evolving computer security threats. ESET pioneered and continues to lead the industry in proactive threat detection. ESET NOD32 Antivirus, its flagship product, consistently achieves the highest accolades in all types of comparative testing and is the foundational product that builds out the ESET product line to include ESET Smart Security. ESET Smart Security is an integrated antivirus, antispyware, antispam and personal firewall solution that combines accuracy, speed and an extremely small system footprint to create the most effective security solution in the industry. Both products have an extremely efficient code base that eliminates the unnecessary large size found in some solutions. This means faster scanning that doesn’t slow down computers or networks. Sold in more than 160 countries, ESET has worldwide production headquarters in Bratislava, SK and worldwide distribution headquarters in San Diego, U.S. ESET also has offices in Bristol, U.K.; Buenos Aires, AR; Prague, CZ; and is globally represented by an extensive partner network. For more information, visit our local office at https://eset.version-2.sg.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The Company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which includes Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities. For more information, please visit https://www.version-2.com.sg/ or call (65) 6296-4268.

