ESET takes part in global operation to disrupt Lumma Stealer, one of the most prevalent infostealers
Created: 2025-05-26 03:16:52
- ESET took part in a globally coordinated operation to disrupt Lumma Stealer.
- The operation, led by Microsoft, targeted Lumma Stealer infrastructure, including all known C&C servers from the past year, making the botnet, in large part, inoperative.
- Lumma Stealer has been one of the most prevalent infostealers over the past two years.
- ESET provided both technical analysis and statistical information, and extracted essential data from tens of thousands of samples, as Lumma Stealer developers had been actively developing and maintaining the malware.
BRATISLAVA, PRAGUE — May 21, 2025 — ESET has collaborated with Microsoft, BitSight, Lumen, Cloudflare, CleanDNS, and GMO Registry in a global disruption operation against Lumma Stealer, an infamous Malware- as- a- Service infostealer. The operation targeted Lumma Stealer infrastructure, specifically all known C&C servers of the past year, making the botnet, in large part, inoperative.
“ESET automated systems processed tens of thousands of Lumma Stealer samples, dissecting them to extract key elements, such as C&C servers and affiliate identifiers. This allowed us to continuously monitor Lumma Stealer’s activity, cluster affiliates, keep track of development updates, and more,” says ESET researcher Jakub Tomanek, who monitors and investigates Lumma Stealer. “Infostealer malware families, like Lumma Stealer, are typically just a foreshadowing of future, much more devastating attacks. Harvested credentials are a valued commodity in the cybercrime underworld, sold by initial access brokers to various other cybercriminals, including ransomware affiliates,” adds Tomanek. Lumma Stealer has been one of the most prevalent infostealers over the past two years, leaving no part of the world untouched.
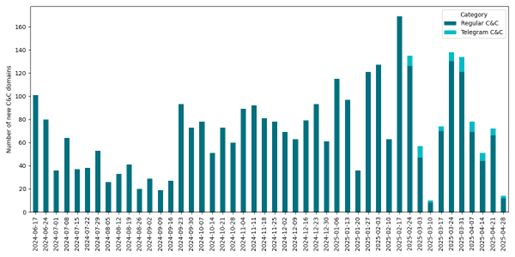
Lumma Stealer developers had been actively developing and maintaining the malware. ESET has regularly spotted code updates ranging from minor bugfixes to complete replacement of string encryption and updates to the network protocol. The operators of the botnet also actively maintained the shared network infrastructure. Between June 17, 2024 and May 1, 2025, ESET observed a total of 3,353 unique C&C domains, with an approximate average of 74 new domains emerging each week, including occasional updates to Telegram-based dead drop resolvers. This ongoing evolution underscores the significant threat posed by Lumma Stealer and highlights the importance of the disruption efforts.
Lumma Stealer adopts the concept of malware as a service, where affiliates pay a monthly fee based on their tier to receive the latest malware builds and the network infrastructure necessary for data exfiltration. The tiered subscription model features price ranges from $250 to $1000 per month, each with increasingly sophisticated features. The operators of Lumma Stealer have also created a Telegram marketplace for affiliates, with a rating system to sell stolen data without intermediaries. Common distribution methods include phishing, cracked software, and other malware downloaders. Lumma Stealer employs a few, but effective, anti-emulation techniques that make analysis as complicated as possible. These techniques are designed to evade detection and hinder the efforts of security analysts.
Microsoft’s Digital Crimes Unit has facilitated the takedown, suspension, seizure, and blocking of the malicious domains that formed the backbone of Lumma Stealer’s infrastructure via a court order granted by the United States District Court of the Northern District of Georgia. In coordination, the U.S. Department of Justice simultaneously also seized the Lumma Stealer control panel, targeting the Lumma Stealer marketplace – and in turn the purchasers of Lumma Stealer malware. This was coordinated with Europol’s European Cybercrime Center (EC3) as well as Japan’s Cybercrime Control Center (JC3), which facilitated the suspension of locally based Lumma Stealer infrastructure.
“This global disruption operation was made possible by our long-term tracking of Lumma Stealer. The disruption led by Microsoft aimed to seize all known Lumma Stealer C&C domains, making the exfiltration infrastructure of Lumma Stealer non-functional. However, ESET will continue to track other infostealers while closely monitoring for Lumma Stealer activity following this disruption,” concludes Tomanek.
For an overview of the Lumma Stealer ecosystem and both a technical analysis and look at the evolution of Lumma Stealer's key static and dynamic properties critical to the disruption effort, check out the latest ESET Research blogpost, “ESET takes part in global operation to disrupt Lumma Stealer” on WeLiveSecurity.com. Make sure to follow ESET Research on Twitter (today known as X), BlueSky, and Mastodon for the latest news from ESET Research.
Lumma Stealer detection rate based on ESET telemetry (data since July 2024)
Weekly counts of new C&C domains
About ESET
ESET develops software solutions that deliver instant, comprehensive protection against evolving computer security threats. ESET pioneered and continues to lead the industry in proactive threat detection. ESET NOD32 Antivirus, its flagship product, consistently achieves the highest accolades in all types of comparative testing and is the foundational product that builds out the ESET product line to include ESET Smart Security. ESET Smart Security is an integrated antivirus, antispyware, antispam and personal firewall solution that combines accuracy, speed and an extremely small system footprint to create the most effective security solution in the industry. Both products have an extremely efficient code base that eliminates the unnecessary large size found in some solutions. This means faster scanning that doesn’t slow down computers or networks. Sold in more than 160 countries, ESET has worldwide production headquarters in Bratislava, SK and worldwide distribution headquarters in San Diego, U.S. ESET also has offices in Bristol, U.K.; Buenos Aires, AR; Prague, CZ; and is globally represented by an extensive partner network. For more information, visit our local office at https://eset.version-2.sg.
About Version 2 Limited
Version 2 Limited is one of the most dynamic IT companies in Asia. The Company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 Limited offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which includes Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities. For more information, please visit https://www.version-2.com.sg/ or call (65) 6296-4268.

